XSS Explained: Learn cross-site scripting with examples
Kurukshetra is an intentionally designed XSS-vulnerable application. XSS is explained with examples, and it's an open-source lab for practicing and learning cross-site scripting vulnerabilities.

You would like to learn more about what a cross-site scripting vulnerability is and how it can be exploited with examples. This is the right place for you. I have compiled short lessons on cross-site scripting (XSS) vulnerability with trial testing scenarios close to real-time, which can help you get started with real-world applications.
Let's start by setting up the lab environment needed for practicing XSS, and upcoming articles will cover the theory and step-by-step approach for identifying the vulnerability.
Kurukshetra- An XSS-vulnerable app by design
In the author's own words, "Kurukshetra is a vulnerable lab geared towards practicing XSS challenges."
The app's motto is to give you hands-on experience in identifying the XSS vulnerability in different ways and also keep you updated about the theory and basics needed.
You can find the repository link given below.

All the content here provided is only for the educational purposes. Authors, Application Creators or Web Site Owners are not reponsible for misue of your knowledge. You are responsible for your own actions!.
Kurukshetra app isn't for production use — only for testing and learning on a host machine.

Preparing Environment
A couple of things must be done to start working on the "Kurukshetra" XSS vulnerable application.
- Docker & Docker Compose must be installed and working
- A working OS(Linux/Windows/Mac) with network connectivity
- Git installed
Feel free to skip to the next section if all the required tools are pre-installed.
For users whose Docker is not installed, please visit the Get Docker page and follow the instructions as specified.

Once installed, make sure the Docker is working. The output of the command should be something similar to the below output.
Docker check:
docker --versionOutput:
Docker version 20.10.17, build 100c701After installing the Docker, you can set up the docker-compose by referring to the below link. It is needed to build up the environment on the go.

Make sure the docker-compose is working by verifying the version information.
Docker Compose check:
docker compose versionOutput:
Docker Compose version v2.12.2Hopefully, "git" is installed on most of them. If you think you don't have one, just go ahead and install it from your package manager or the link given below.


Lab-Setup - "Kurukshetra" Application 💻
Let's clone the application from the GitHub repository and copy it onto your system.
git clone https://github.com/D4rk36/Kurukshetra.gitNavigate to the downloaded directory.
cd ./KurukshetraInside the directory, you will find a "docker-compose.yml" file, which contains the instructions for running the application. You have to run "docker compose up" to bring up the environment.
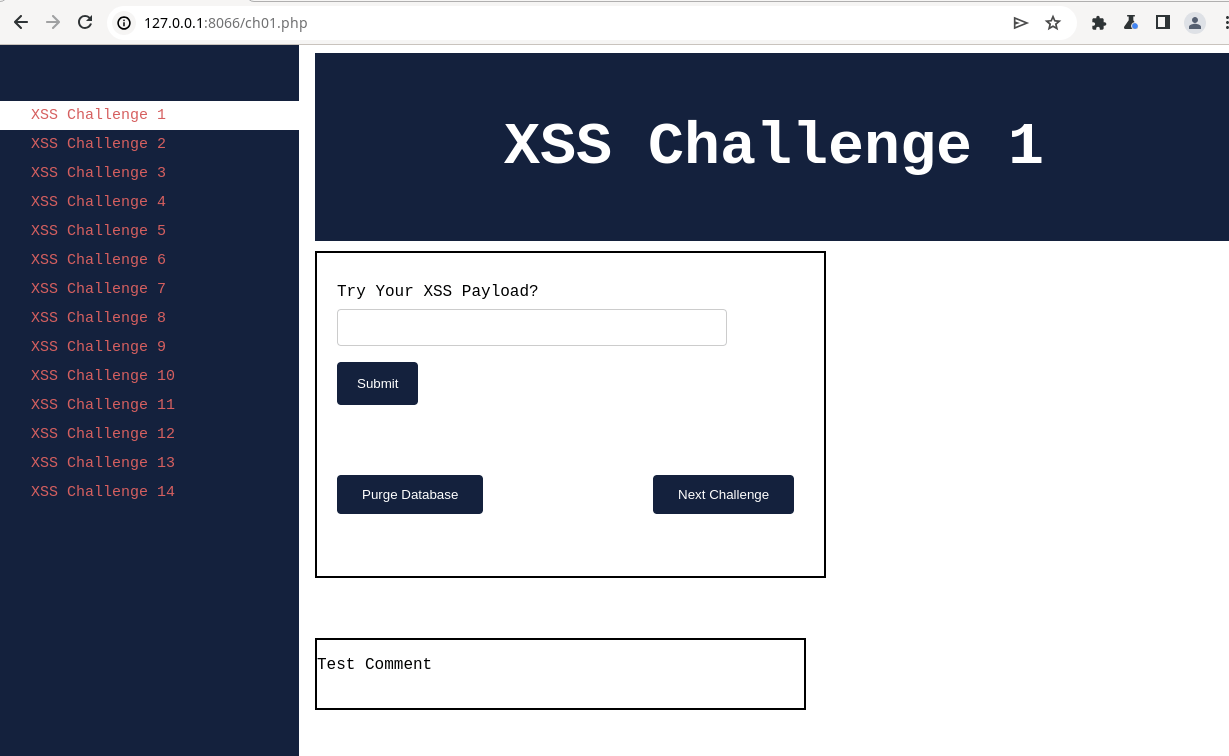
docker compose upOnce the environment is up, let's verify by accessing the app environment by clicking on the following URL: http://localhost:8066/ or paste it into your browser.
The page will be displayed below.
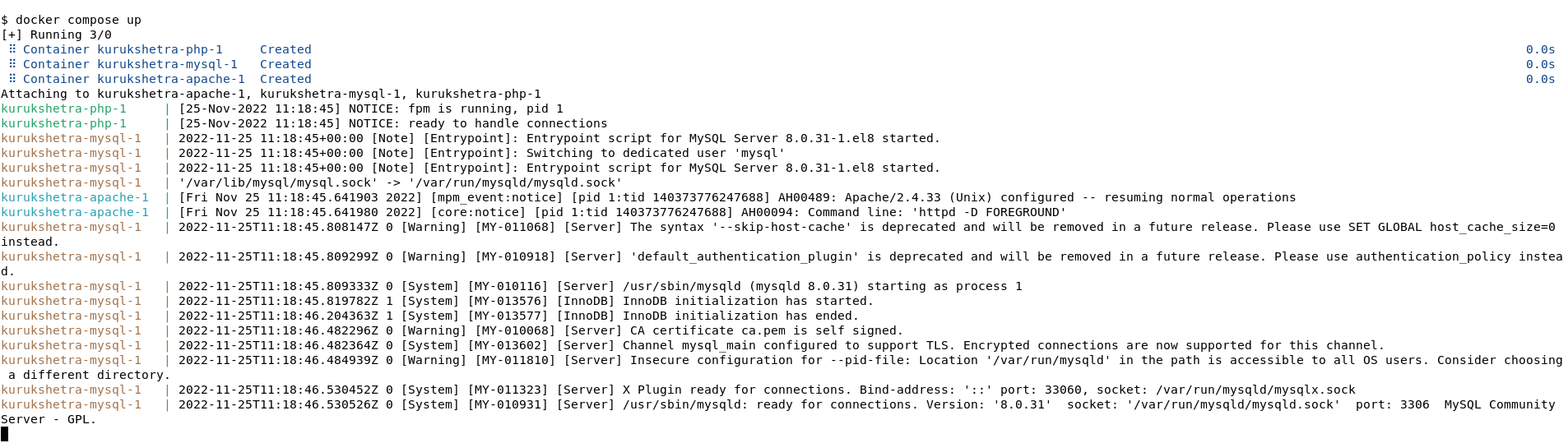
Bringing up the Docker instance might take a couple of minutes, based on your network speeds. You should also be able to see the log as displayed below while starting up.
During any time in the lab, you can run "Ctrl - c" to stop the running environment.
Additionally, to completely remove the "Kurukshetra" containers running from your system, run the remove command from the same directory where the docker-compose.yml file is present.
docker compose rmNow that our lab environment is up and working, you are good to proceed to the next step of identifying the XSS vulnerabilities.

Summary
The setup is straightforward for users who are familiar with Docker. For other users who are new to docker, you might need to get adapted to using it. Most of the tools are now being containerized to avoid the installation process. Just download and run with docker.
Ensure your lab environment is working to jump-start learning about cross-site scripting vulnerability. The next articles will cover types of cross-site scripting vulnerabilities and techniques used to identify them. 😃

