WordPress Scan for Vulnerabilities: A Comprehensive Guide for Site Security
WordPress scan for vulnerabilities article will guide you with step-by-step approaches and examples that can be implemented on your website to scan and identify vulnerabilities. Also, additional information about security measures, tools, and plugins is available.

WordPress scan for vulnerabilities article will guide you with step-by-step approaches and examples that can be implemented on your website to scan and identify vulnerabilities. Additionally, you will discover the importance of performing regular scans and reducing potential risks by implementing the suitable security measures, tools, and plugins available. Empower yourself with the knowledge and tools to maintain a secure and resilient WordPress website.
Understanding the Importance of Vulnerabilities Scans
In today's digital age, the attack landscape for WordPress sites is constantly evolving. Cybercriminals are always looking for new ways to exploit vulnerabilities and compromise the security of websites. As a WordPress website owner, securing the business and customer data hosted on your website is crucial.
Below are statistics of the most infected CMS websites in 2022 by Sucuri.
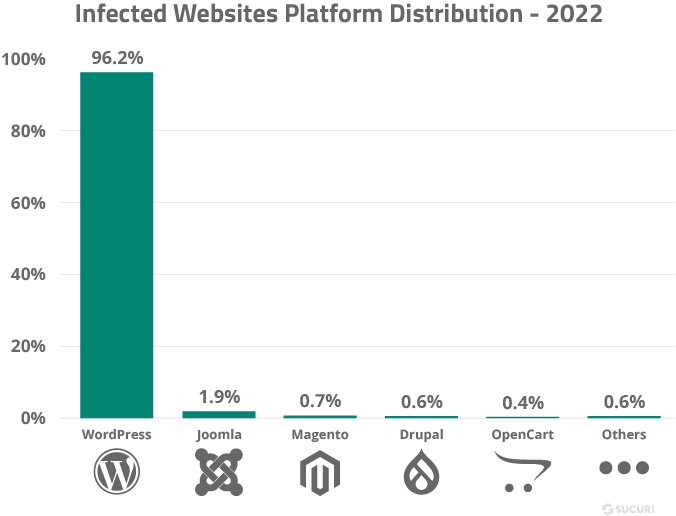
Evolving Landscape of WordPress Vulnerabilities in Cyber Security
Cyber threats are becoming more sophisticated than ever. Coming to WordPress, new vulnerabilities are primarily discovered in third-party plugins, and some are in themes and WordPress core. Attackers leverage these vulnerabilities to gain unauthorized access to your website, spread malware, steal sensitive information, or even disrupt the functionality of your site. As a result, proactive measures can help you to address these vulnerabilities before they are exploited.
Below are statistics on vulnerabilities based on WordPress components by wpscan.
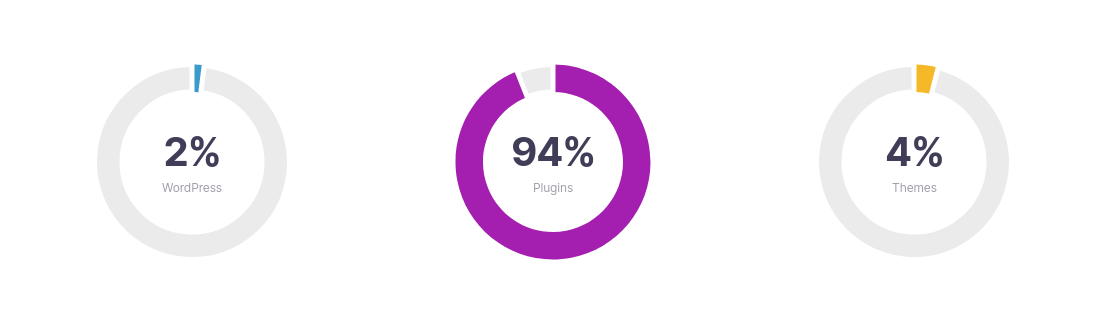
Risks of ignoring security measures
Ignoring security measures for your WordPress site can have severe consequences. A compromised website can lead to a loss of customer trust, damage to your brand's reputation, and potential legal and financial implications.
Additionally, the time and resources required to recover from a security breach can substantially impact your business operations and revenue.
Benefits of proactive vulnerability scanning
Proactively scanning your WordPress site for vulnerabilities offers several benefits.
- It allows you to identify and address potential security risks before malicious actors exploit them.
- Vulnerability scans also help you maintain compliance with security standards and regulations.
- It demonstrates your commitment to protecting user data and maintaining a secure online environment.
Choosing the Right Tools or Plugins for Vulnerabilities Scans
When performing vulnerability scans for your WordPress site, choosing the right tools or using the recommended security plugins is crucial. Going ahead, I will cover different options available to scan a website for security flaws. Pick the one that matches your requirements and capabilities.
Popular vulnerability scanning tools
There are numerous vulnerability scanning tools and plugins designed specifically for WordPress security. Some popular options include plugin-based software such as Jetpack Protect, Wordfence, Sucuri Security, Shield Security, etc. Advanced scanners like Nuclie Scan, WPScan, CMSeek, etc. These tools offer varying levels of security by helping you detect vulnerabilities, malware scanning, firewall protection, and security hardening, and even about how to address vulnerabilities.
Factors to consider when selecting a scanning tool or plugin
Below are some of the factors that can help select a WordPress security scanner, i.e. plugin based or online tool:
- How frequently is the vulnerability database being updated?
- What level of support and documentation is available?
- Does the tool offer additional specific features like securing login, APIs, enabling firewalls, notifications, Two-Factor Authentication, etc?
- What is the expected budget vs the tool cost structure?
- How effective is it in identifying the vulnerabilities?
- Does it support automation and regular interval scans?
- How many of your websites need to be protected?
- How big is your application, and how many custom-coded functionalities are used?
Above are a few points that help you to select the one that aligns with your website's security needs. It's important to choose a tool that provides comprehensive scanning capabilities and is regularly updated to address new threats.
Comparing free vs. paid scanning options
While most examples covered in this article will use the free vulnerability scanning tools available, it's important to weigh the benefits before investing in a paid solution. Paid options often provide advanced features, dedicated support, and enhanced protection, making them a worthwhile investment for the security of your WordPress site.
Preliminary Steps Before Performing a Vulnerabilities Scan
Now that you understand the importance of vulnerability scanning, the most important step is to ensure your data is safe and ready to restore at any point in time.
Backup all your WordPress site
Before carrying out any security checks, the first thing to do is to ensure that a complete website backup is taken and can be easily restored. This precautionary measure will be helpful in case any unexpected issues arise. Therefore, data integrity should never be compromised.
Additionally, the backup should be hosted on a separate server, different from the one where you are performing the security scan.
Update your WordPress site before the scan
In most cases, a simple solution to fix the vulnerabilities would be to update the plugins, theme, and WordPress core. Of course, if you have customized any of the code, you might need to check the compatibility before updating.
This step can save efforts and can avoid dealing with vulnerabilities to which the vendor has already provided patches. Therefore, our results will be more accurate.
Step-by-Step Guide to Perform Vulnerabilities Scan
In this section, we will explore a variety of WordPress vulnerability scanners (i.e., free or partially free) that are readily accessible on the Internet. We will begin with those that are easy to use and then move to advanced CLI scanners.
Using WPSEC: Automated WordPress Scanner (Online)*
WPSec is one of the WordPress security scanners out there on the internet. You can perform a WordPress vulnerability scan online. There is no need to set up any tools. Start right with the scan.
WPSec is an automated tool that instantly scans your WordPress website for vulnerabilities. It is an advanced vulnerability scanner that utilizes WPScanner and custom technology to continuously update its database with the latest security features and bug fixes.
The tool offers both free and paid plans. For demo purposes, we will use a free plan.
Visit the site https://wpsec.com, provide the URL of the WordPress website that you own, and click on the "Start Scan" button. I will be using my test website as an example here.
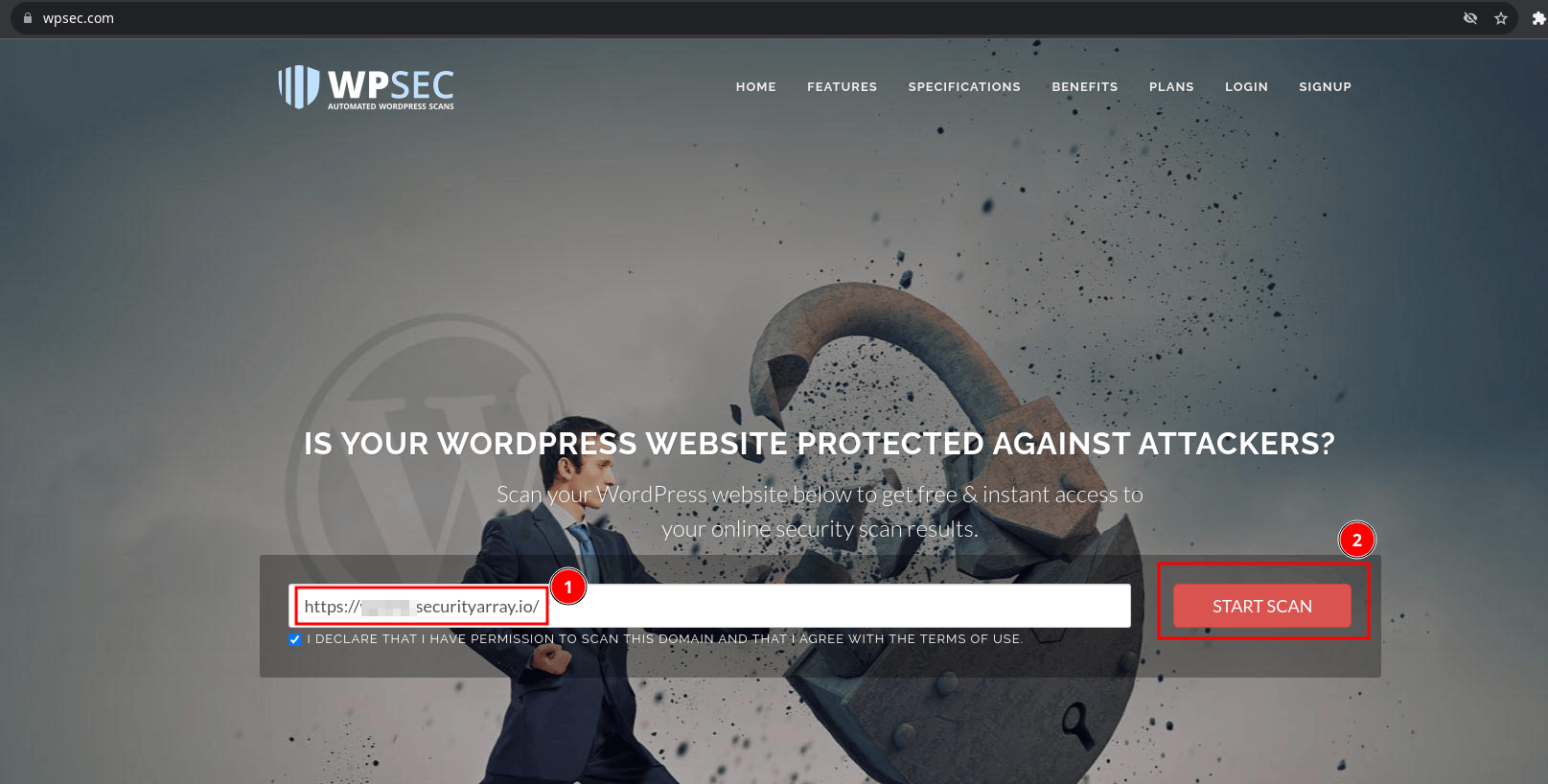
It takes a few minutes or less to scan the site, and it immediately displays the risk information if your website contains any vulnerable WordPress components.
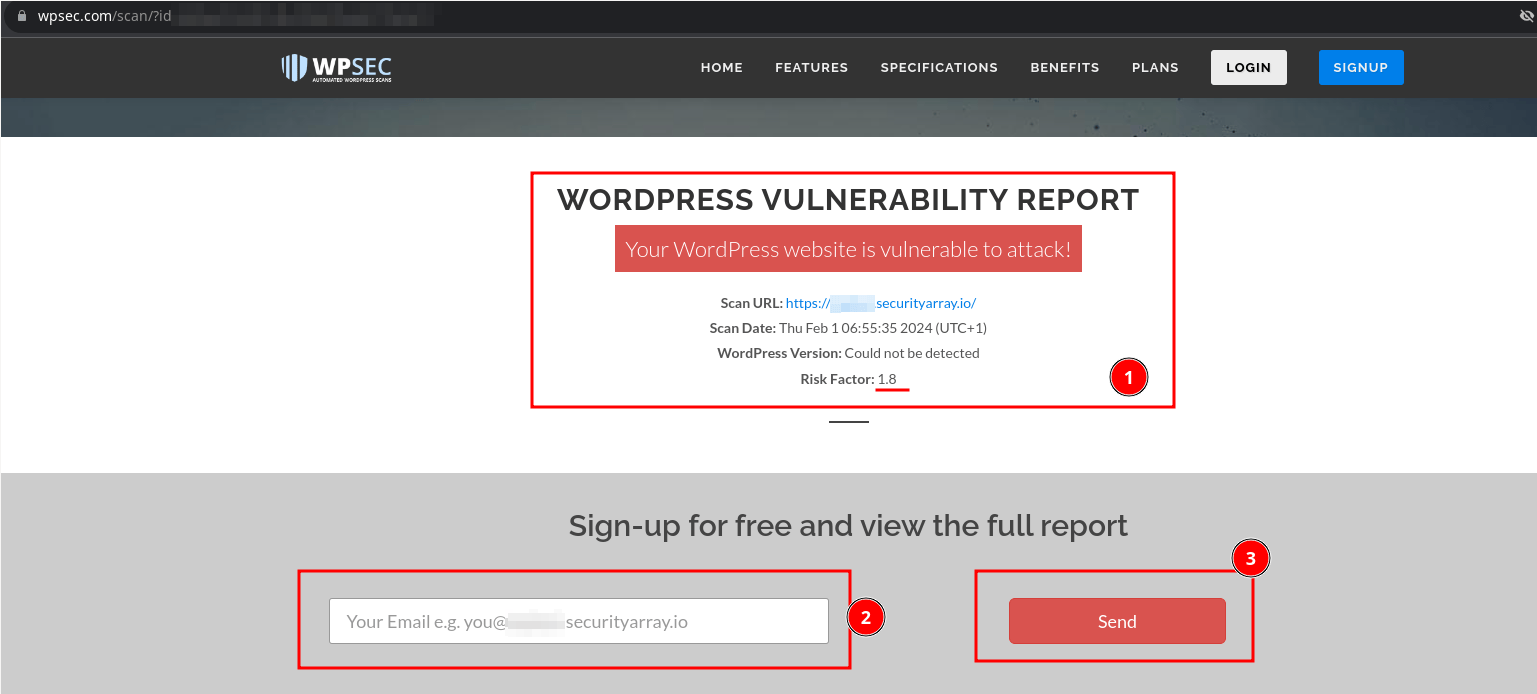
On my website, I can see that it displays the message "Your WordPress website is vulnerable to attack!" and the Risk Factor is 1.8, which indicates that security flaws exist and can be used to compromise the site.
To access the vulnerabilities report and to carry out regular interval scans, one must register using a valid email address of the same domain. You can give an email address and click the "Send" button to complete the "Sign Up" process.
Upon successfully logging into the application, authenticated users will have a dashboard displaying the total number of WordPress sites added to their WPSEC account.
On the left side of the tab, click on the "View Reports" link as displayed below.
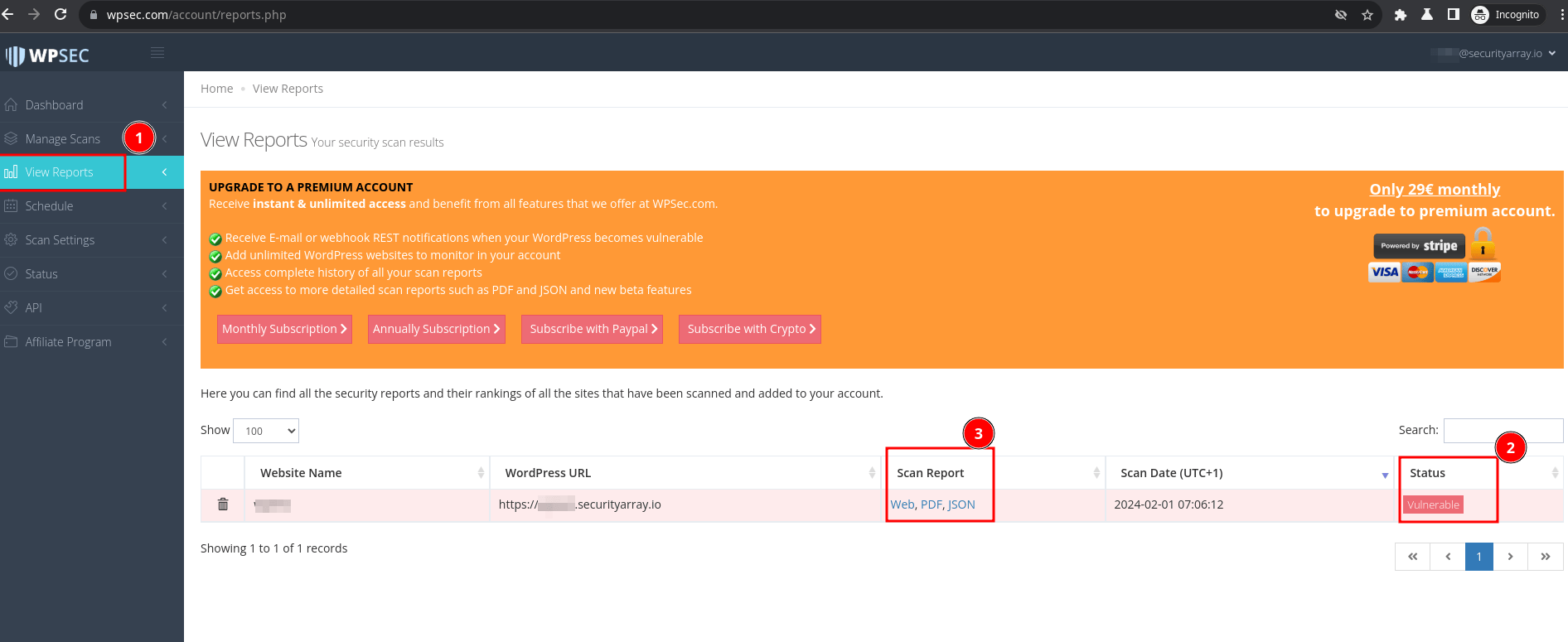
From the above screen, we can see that my site status is displayed as "Vulnerable" and can see the scan reports in web, PDF and JSON formats. Only "web" reports are available in the free edition, and another type of report would require you to upgrade to a premium account.
Click on the "Web" report and scroll down to the "Plugins & Themes" section, where you can find the information on identified vulnerabilities that could potentially impact the site.
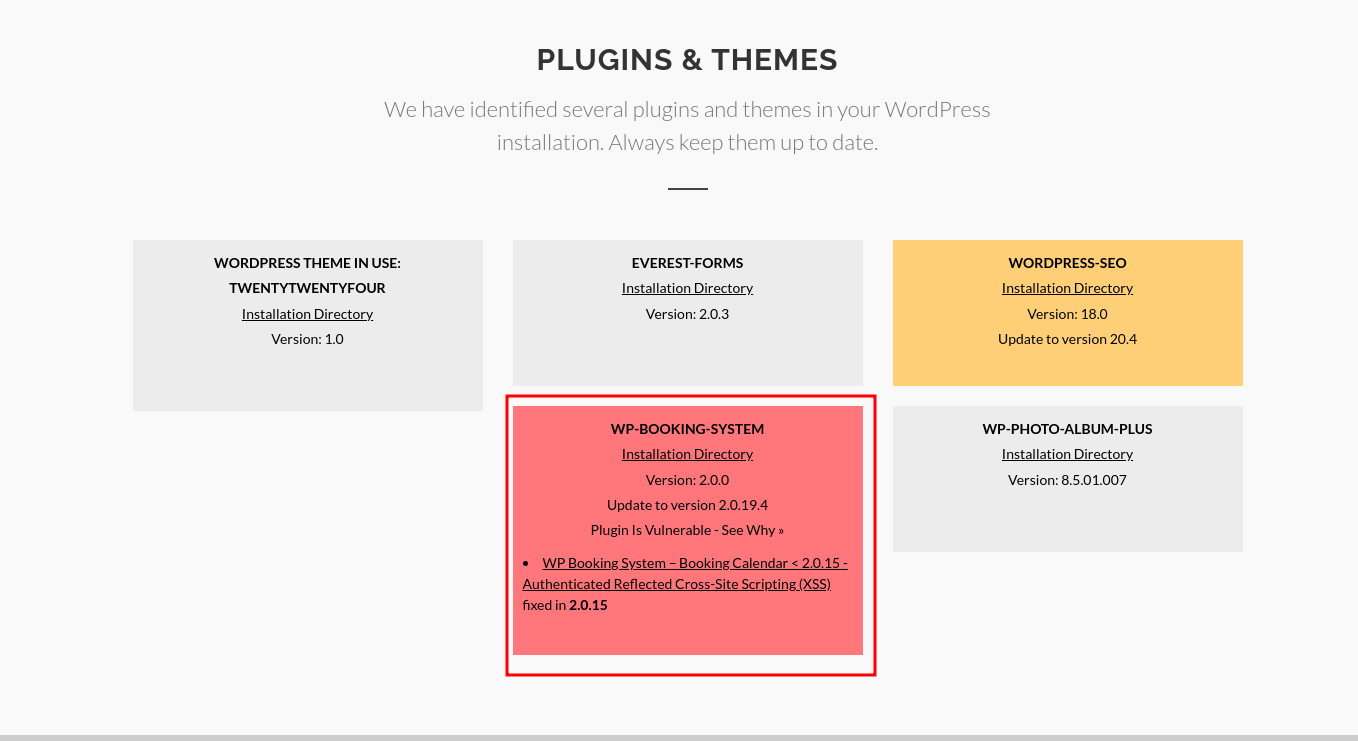
Toggle on the "WP-Booking-System" vulnerable plugin highlighted in red, and the additional vulnerability information is displayed. It displays the "Reflected Cross-Site-Scripting Vulnerability" present in the plugin being used.
Just click on the link, and it will take you to another page displaying more detailed information about the vulnerability and proof of concept (POC) on how it can be exploited.
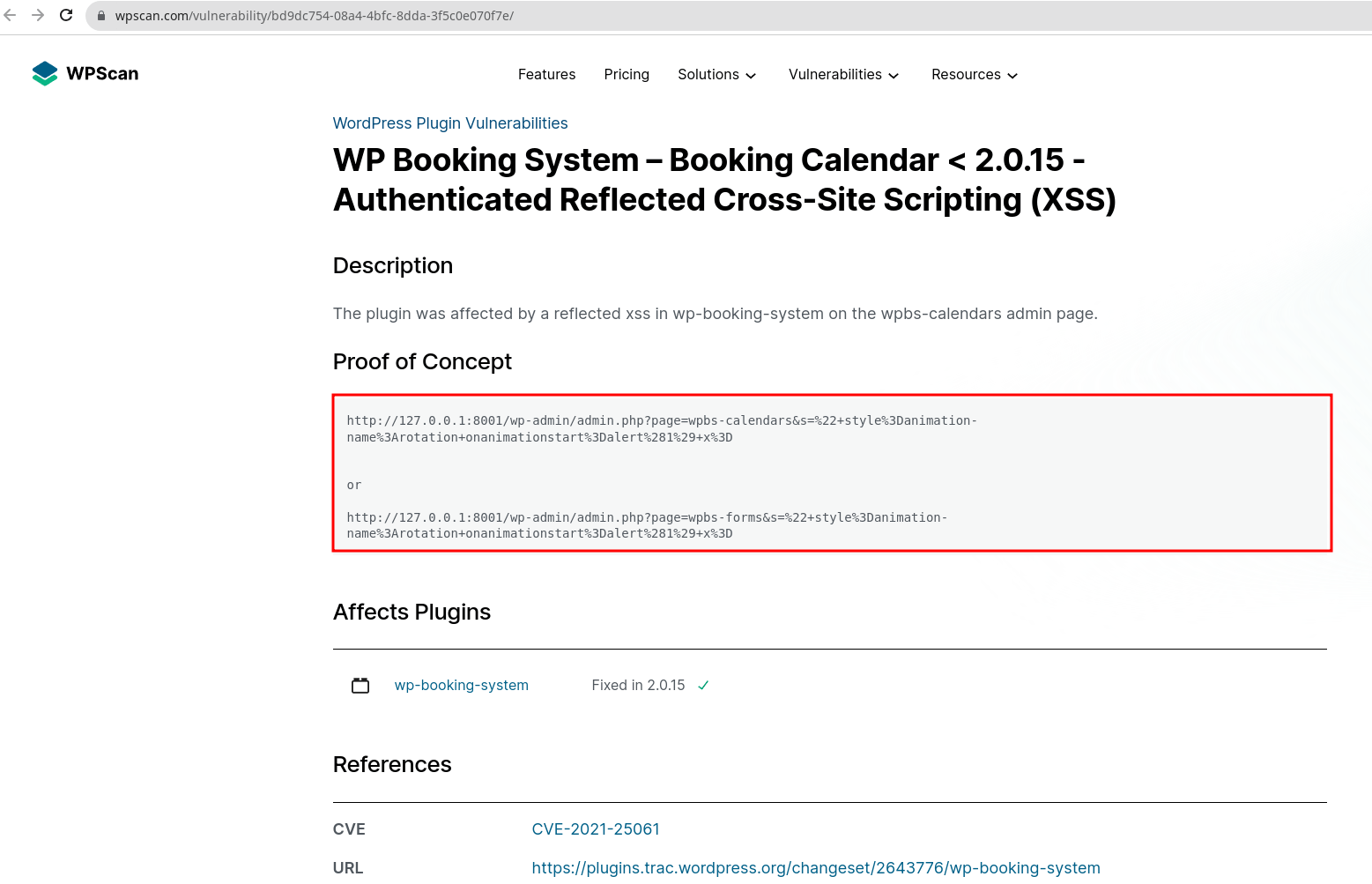
From the security analyst's point of view, the above information can help to verify and confirm the vulnerability.
Attackers use the same vulnerability by modifying the above code to redirect genuine users to a malicious website, steal session cookies, to log keystrokes, for phishing, etc.
From a website owner's perspective, Based on the above recommendations, the following vulnerability can be fixed by upgrading the "WP-Booking-System" plugin to its latest version, i.e. "2.0.15". Therefore, we must update the wp-booking-system plugin to the latest version to avoid security impact.
Identify similar security vulnerabilities early and fix them as early as possible. If you use the custom code, make sure the code is patched as per recommendations.
Scheduling is one of the built-in features offered by the WPSEC in the free version, which you can continuously monitor and get regular updates about the vulnerabilities found.
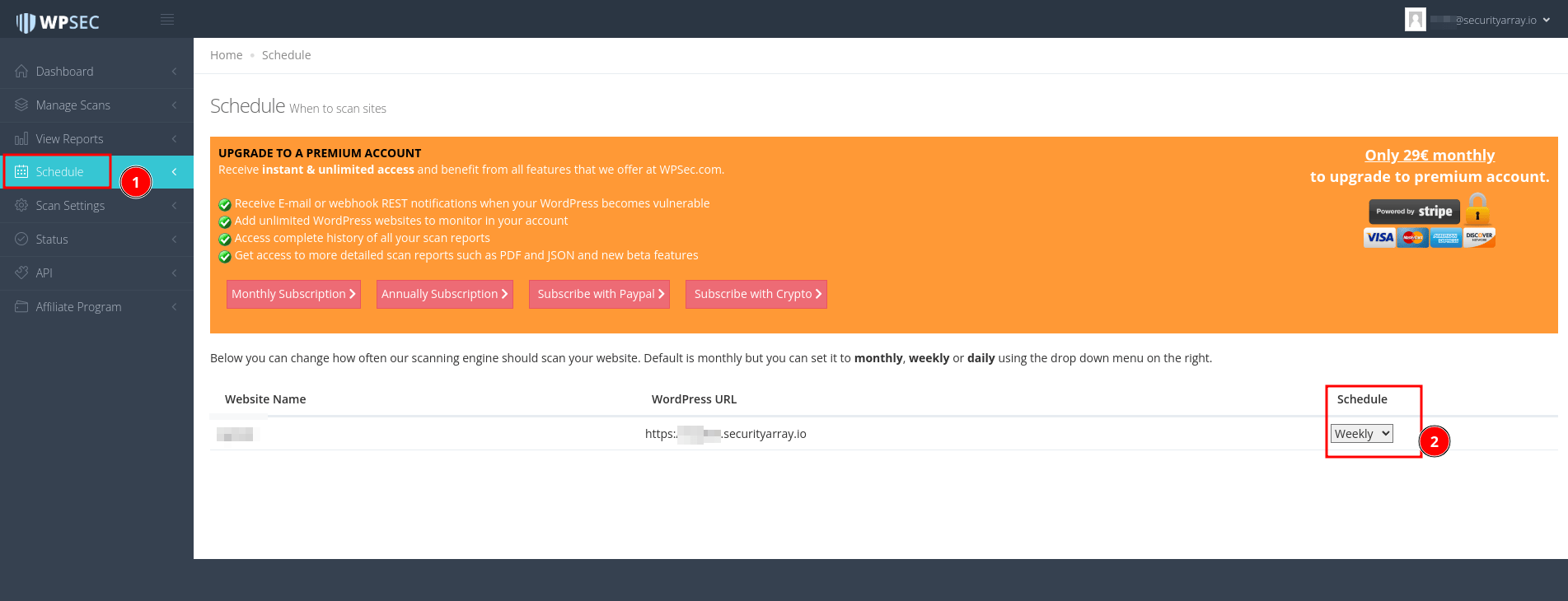
To verify, navigate to the "Schedule" section and ensure the regular scan frequency is set to "Weekly".
One of the things I found about this tool is it reported fewer vulnerabilities compared to other tools. We need to wait and watch if more coverage will be addressed in future scan results.
You could repeat the steps you learnt to find WordPress vulnerabilities on your websites.
Using Jetpack Protect: WordPress Malware and Security Scanning (Plugin)
A WordPress plugin that can help you scan for malware and security vulnerabilities associated with WordPress Core, themes and plugins.
This would be the second tool that we would be using to scan for WordPress threats.

The plugin is simple and easy to use.
Jetpack Protect is a totally free plugin that uses the data from WPScan. It is one of the most popular tools used in the security industry to carry out vulnerability scans on WordPress websites.
Let's jump right into setting up the plugin.
Log into your WordPress website admin dashboard, Navigate to the plugins section and click the "Add New Plugin" button.
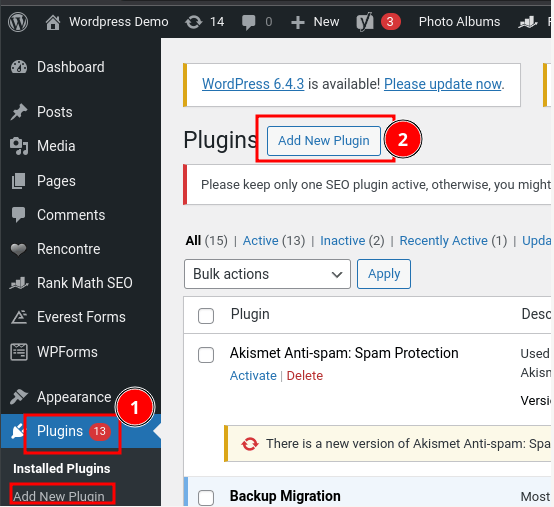
The website loads a plugin page and displays all commonly installed plugins.
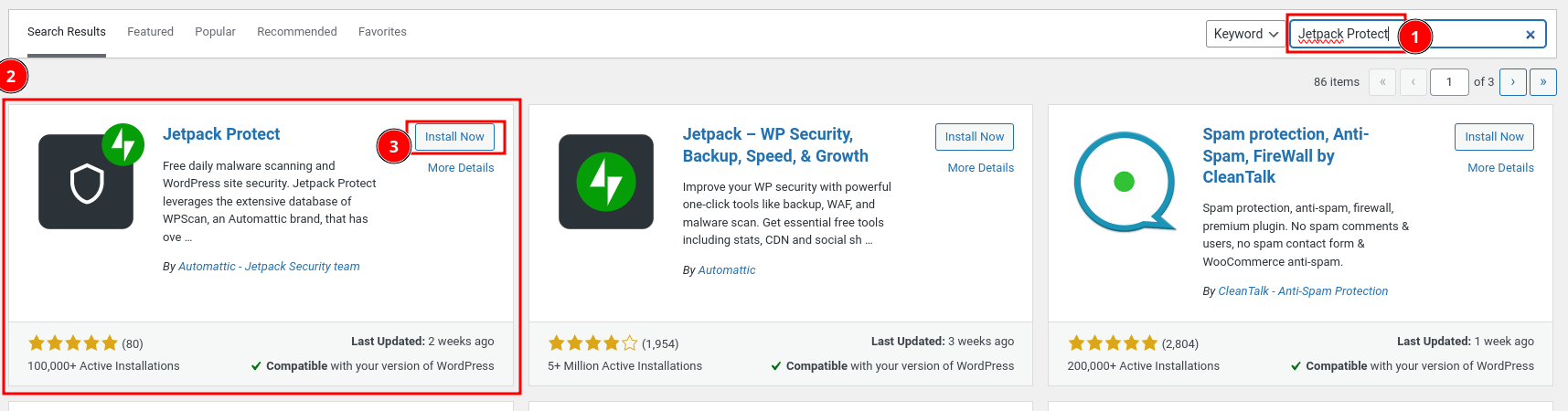
Search for the "Jetpact Protect" plugin and click on the "Install Now" button.
Ensure that you install the plugin offered by the "Automattic - Jetpack Security team."
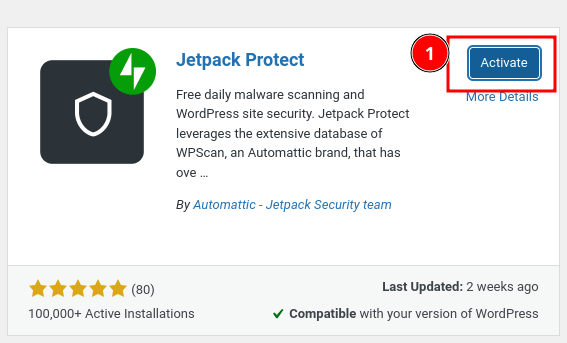
Once installed, click on the "Activate" button as displayed above.
After activation, you will be taken to a subscription page. For demonstration purposes, I will click on the "Start for free" button to go ahead. Feel free to explore the premium options as well.
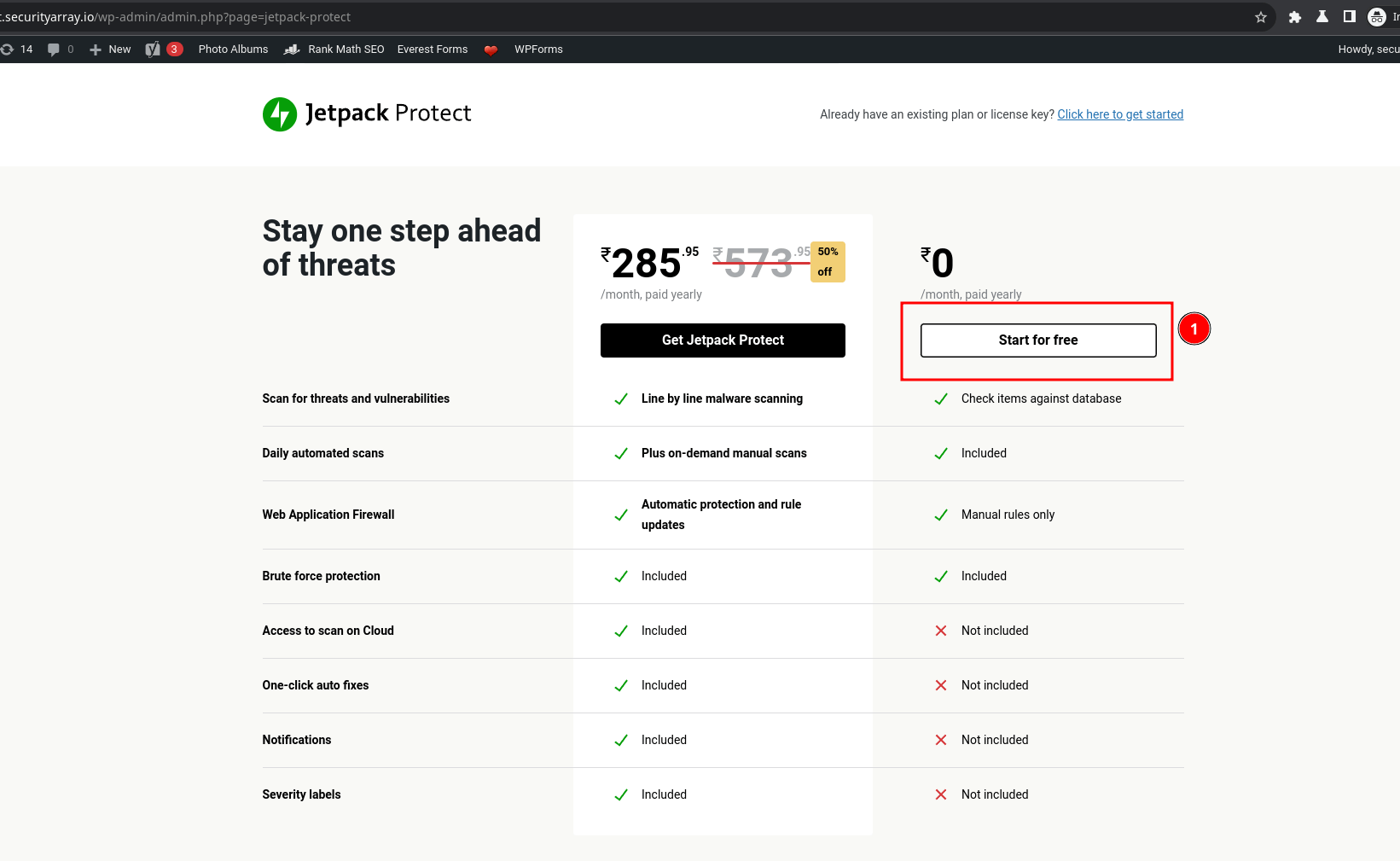
Once activated, it will immediately start scanning your site for vulnerabilities. It might take a couple of minutes.
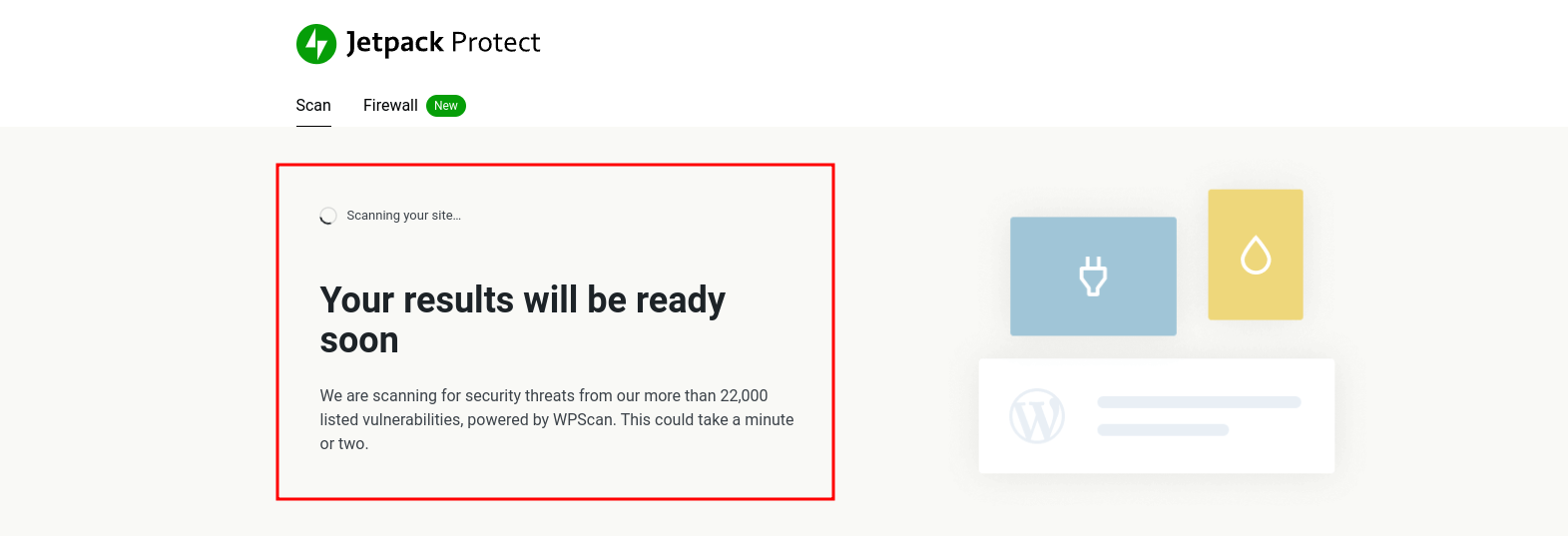
After successful completion, all the identified threats are displayed, as shown below.
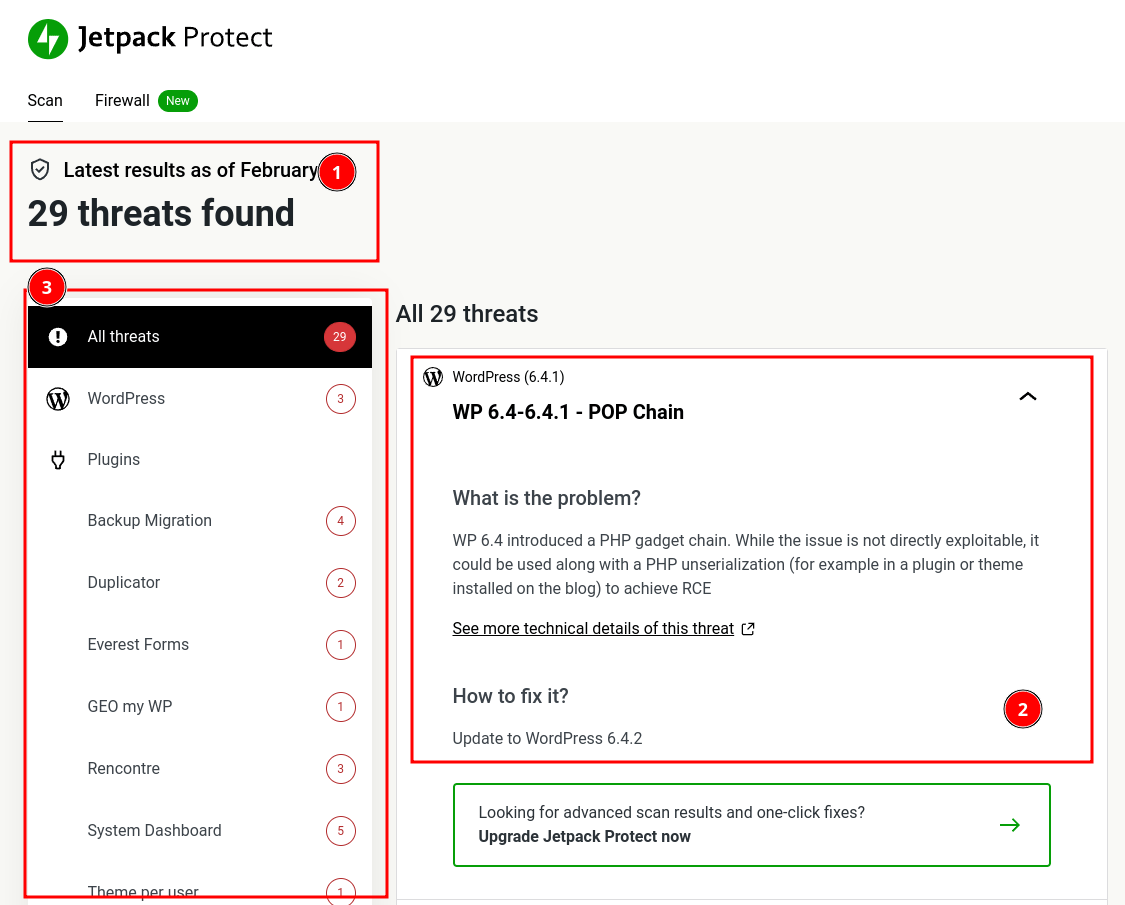
The plugin identified 29 threats on my website, listed above in detail. Additionally, the summary information about each threat is displayed on the right side, which helps you take the next action needed to secure your site.
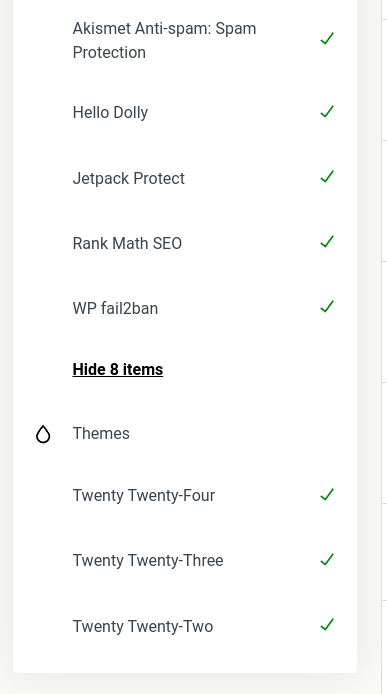
It also displays a green checkmark for plugins, themes, and core if they are free from threats.
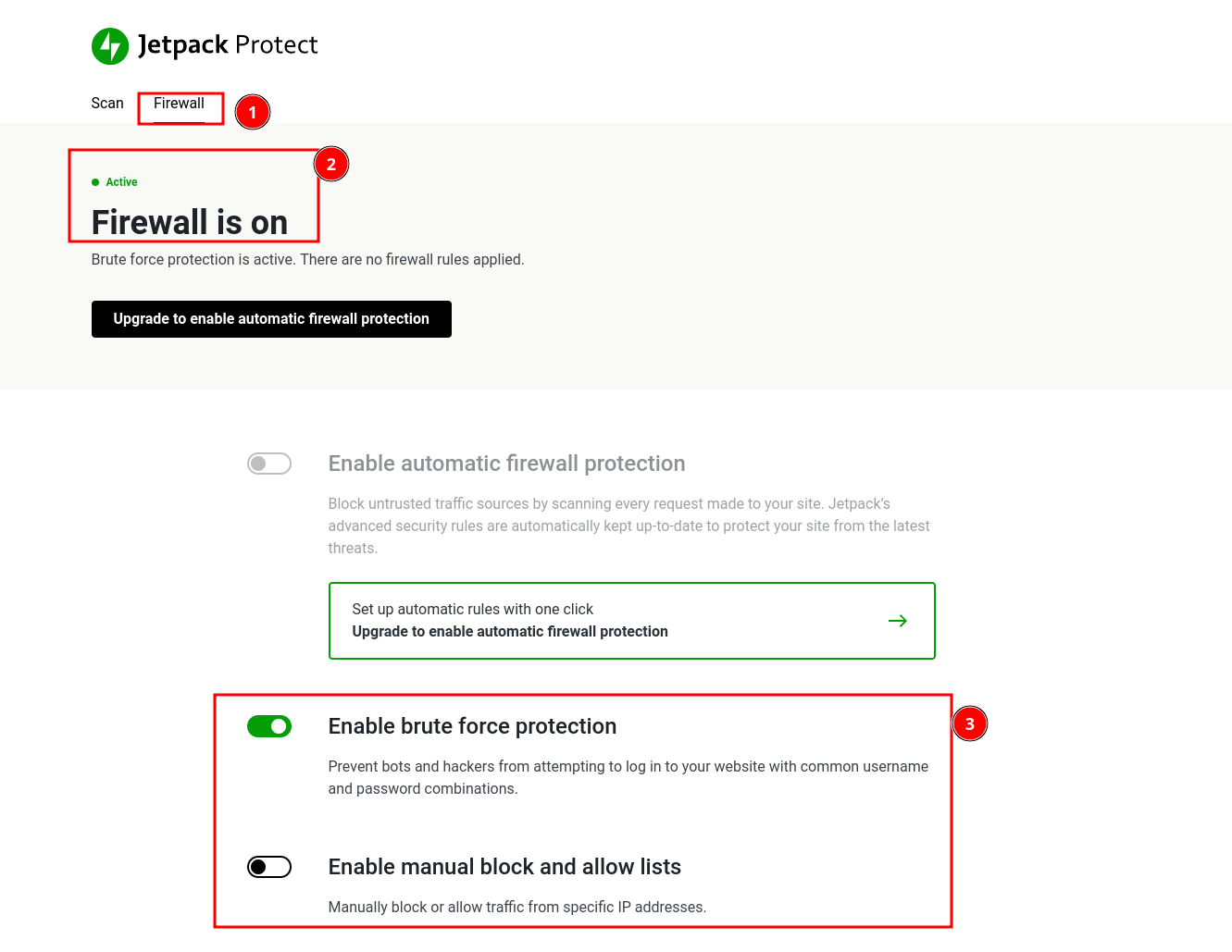
Jetpack Protect even allows you to set up a "Firewall" for your site; feel free to explore. I have just enabled the Firewall to prevent the brute force attacks on my site's login page, as shown below.
The Jetpack protect plugin is one of the effective ways to secure your website. The plugin is well-suited for website owners because of its simplicity and ease of use.
WPScan CLI
Using the Jetpack plugin is a good option when you have admin access to the WordPress website.
WPScan CLI will be used for one-time scans or security assessments. The advantage of a CLI scan is that it can be used to perform specific checks based on the use case, such as checking only for vulnerable plugins or themes, leaking usernames or config backups, etc.
Its installation is straightforward. To set it up locally, you can use the gem package manager, docker, or brew. Check out WPScan Installation.
As I have a Gem installed on my system, I will use the Gem to install it.
WPScan CLI Installation: (Using Gem)
gem install wpscanOutput:
Fetching public_suffix-5.0.5.gem
Successfully installed public_suffix-5.0.5
Successfully installed wpscan-3.8.25
Parsing documentation for public_suffix-5.0.5
Installing ri documentation for public_suffix-5.0.5
Parsing documentation for wpscan-3.8.25
Done installing documentation for public_suffix, wpscan after 0 seconds
2 gems installedWPScan Installation Log
The WPScan CLI tool uses the WordPress Vulnerability Database API to retrieve WordPress vulnerability data in real-time. The --api-token option requires supplying an API token, which can be obtained by registering an account on WPScan.com.
You can use the CLI tool without an API token as well. Only the vulnerability information will be missing.
WPScan using CLI
$ wpscan --url https://wptest.securityarray.io/ -e vp,vt --plugins-detection mixed --api-token $WPSCAN_API_TOKEN- "--url": The target website to scan for vulnerabilities.
- "-e": Enumerating only for vulnerable plugins and templates.
- "--plugins-detection": Using both passive and aggressive ways to detect valid plugins on the website.
- "--api-token": Stored WPScan API token in environment variables and used it for the scan. (You can directly place your API Token Here).
Output Log (Log is stripped.)
[+] URL: https://wptest.securityarray.io/ [xx.xxx.xx.xxx]
...
[+] ninja-forms
| Location: https://wptest.securityarray.io/wp-content/plugins/ninja-forms/
| Last Updated: 2024-03-29T15:38:00.000Z
| Readme: https://wptest.securityarray.io/wp-content/plugins/ninja-forms/readme.txt
| [!] The version is out of date, the latest version is 3.8.2
|
| Found By: Known Locations (Aggressive Detection)
| - https://wptest.securityarray.io/wp-content/plugins/ninja-forms/, status: 200
|
| [!] 2 vulnerabilities identified:
|
| [!] Title: Ninja Forms Contact Form < 3.8.1 - Publicly Accessible Form Submission Export via CSRF
| Fixed in: 3.8.1
| References:
| - https://wpscan.com/vulnerability/9107e702-e5ef-4328-8265-2a6b98092b3a
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-2113
| - https://www.wordfence.com/threat-intel/vulnerabilities/id/3ebfc9f5-abb7-47bc-bd38-f60df1cccb5d
|
| [!] Title: Ninja Forms Contact Form < 3.8.1 - Author+ Stored XSS
| Fixed in: 3.8.1
| References:
| - https://wpscan.com/vulnerability/c89ce032-c361-49e2-8ed0-c806bf399d96
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-2108
| - https://www.wordfence.com/threat-intel/vulnerabilities/id/6a6eb430-cf86-4e13-a4f7-173fada9fddf
|
| Version: 3.8.0 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - https://wptest.securityarray.io/wp-content/plugins/ninja-forms/readme.txt
...WPScan CLI Log
The scans will take a few minutes to complete, and once they are completed, you can check the identified vulnerabilities displayed above.
Using Wordfence Security Plugin
Like Jetpack, Wordfence is another security plugin with many more features that can help scan your WordPress site for known vulnerabilities and malware.
Check out the below bookmark to learn more about the WordFence Security Plugin.

Wordfence WordPress Security Plugin
Offline Tools
In this article, we covered a couple of WordPress vulnerability scanners that are user-friendly and beneficial for website owners. Moving forward, we will discuss one of the customizable vulnerability scanners commonly used by security professionals. Website owners can also consider trying it out for their websites.
Using nuclei: Customizable Vulnerability Scanner
Nuclei is a fast and customizable vulnerability scanner that identifies vulnerabilities based on the YAML-based rules. Nucli is a CLI tool built with Golang, and you would need a Golang installed to run from your local system.
Nuclei alone cannot find vulnerabilities, as it's just an engine that runs any given rules. These rule sets are called as nuclei-templates. By default, the nuclei tool downloads the templates on the first run, so you don't need to download them separately. Both nuclei and nuclei templates are open-source and freely available on GitHub.
To keep things minimal, I will focus only on running the scans on my local demo website. To learn more about the installation and usage of the nuclei tool, check out here.
Default Nuclei Templates vs External Templates
Yes, we can run nuclei scans with the default templates. Default templates are the collection of community contributions with a wide range of vulnerability identification rule sets. Compared to the default one "nuclei-wordfence-cve" templates, which have more WordPress vulnerability identification templates that are taken from the Wordfence reports.
The effectiveness of the Nuclie scanner is directly tied to the quality of the nuclei-templates. The better templates you can find, the better the vulnerabilities. Some security professionals would prefer to write their custom templates.
Nuclei Scan with Nuclei Wordfence CVE Templates
Command:
nuclei -u https://wptest.local -t nuclei-wordfence-cve/ -o results.txt- "nuclei" is the command used to trigger the scan.
- "-u" is the option used to specify the URL of a website which you want the tool to scan for.
- "-t" is to specify a file or folder of templates that need to be used for scanning the given target.
- "-o" is to write the results output to a text file, which can be used further. Check out help information, as other types of results are also available.
Results:
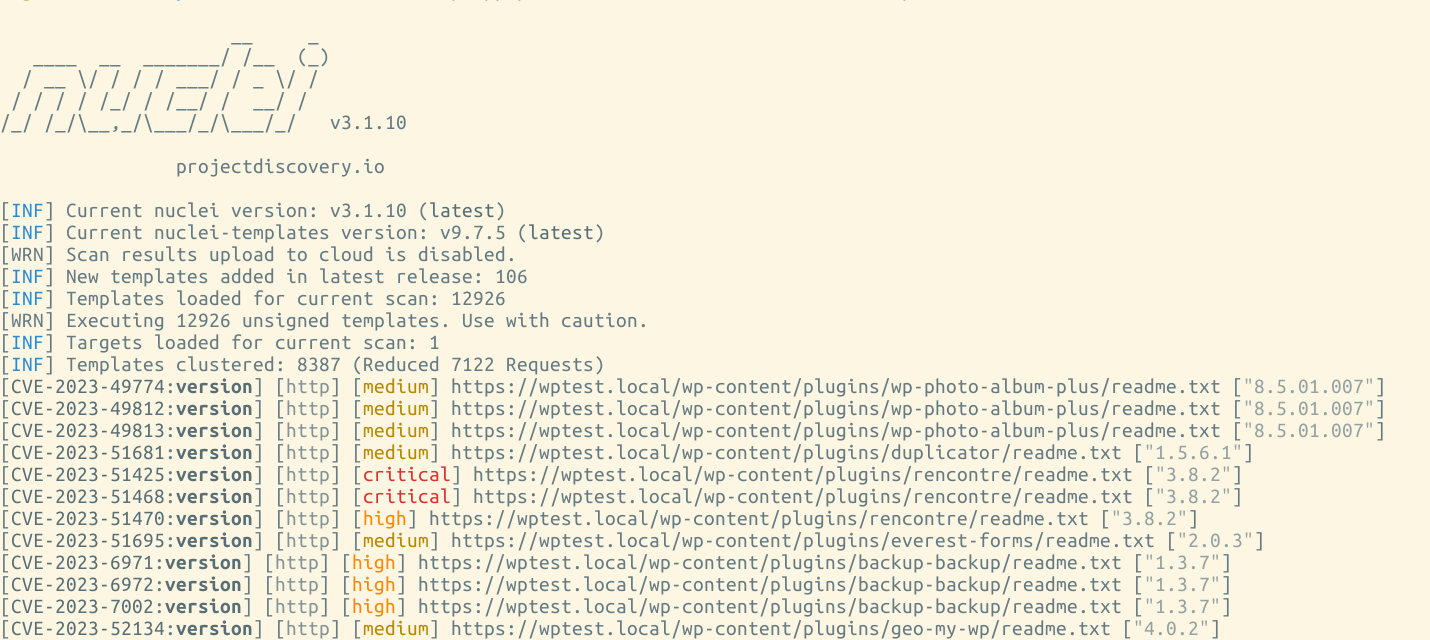
The scan is completed, and a few critical, high, and medium-severity vulnerabilities have been identified on my website.
Command to run Nuclei with default templates
Command:
nuclei -u https://wptest.local -o results.txt -tags wordpress- "-tags" is the command to run specific tag-based templates only. Here, in our command, I am using the keyword called "wordpress".
From the huge list of default templates, only the WordPress-based templates will be loaded for scanning. Give it a try and observe how the vulnerabilities' results differ.
Now, we need to take the CVE IDs and search across Google to find more about that vulnerability and how it can be exploited/mitigated.
For Example: CVE-2023-52134
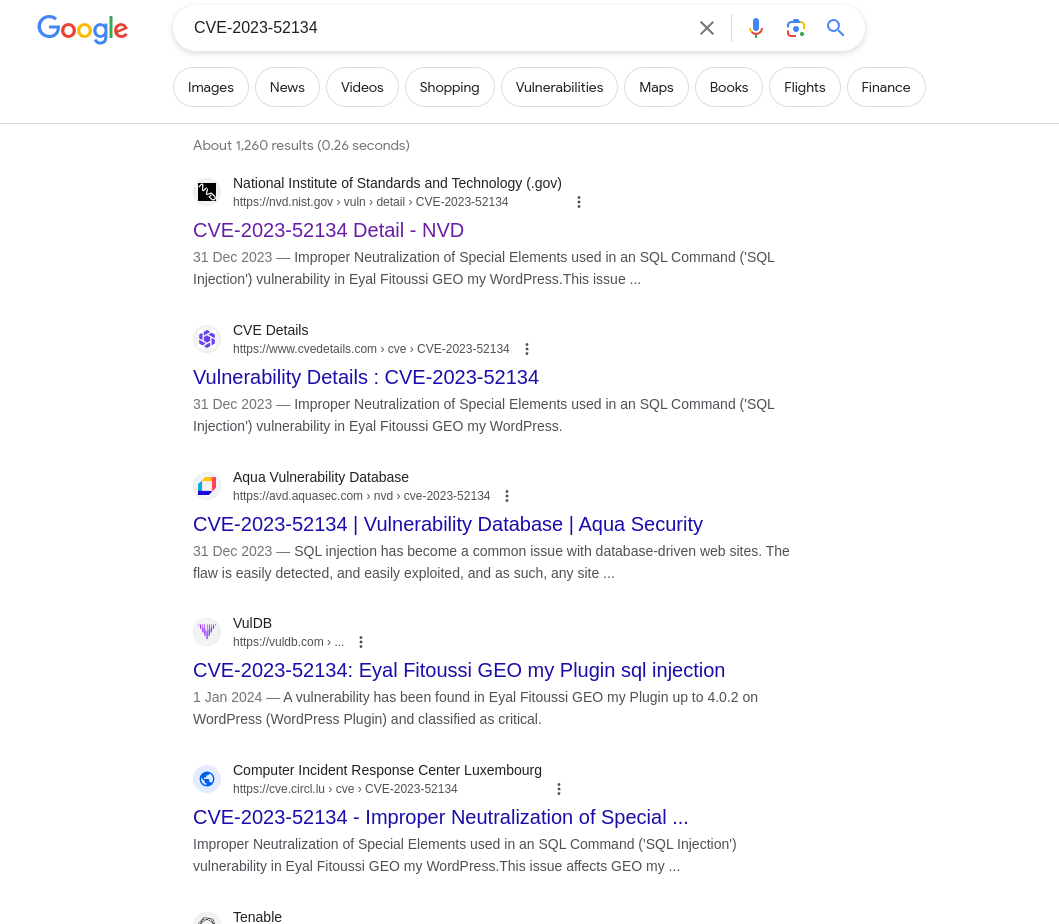
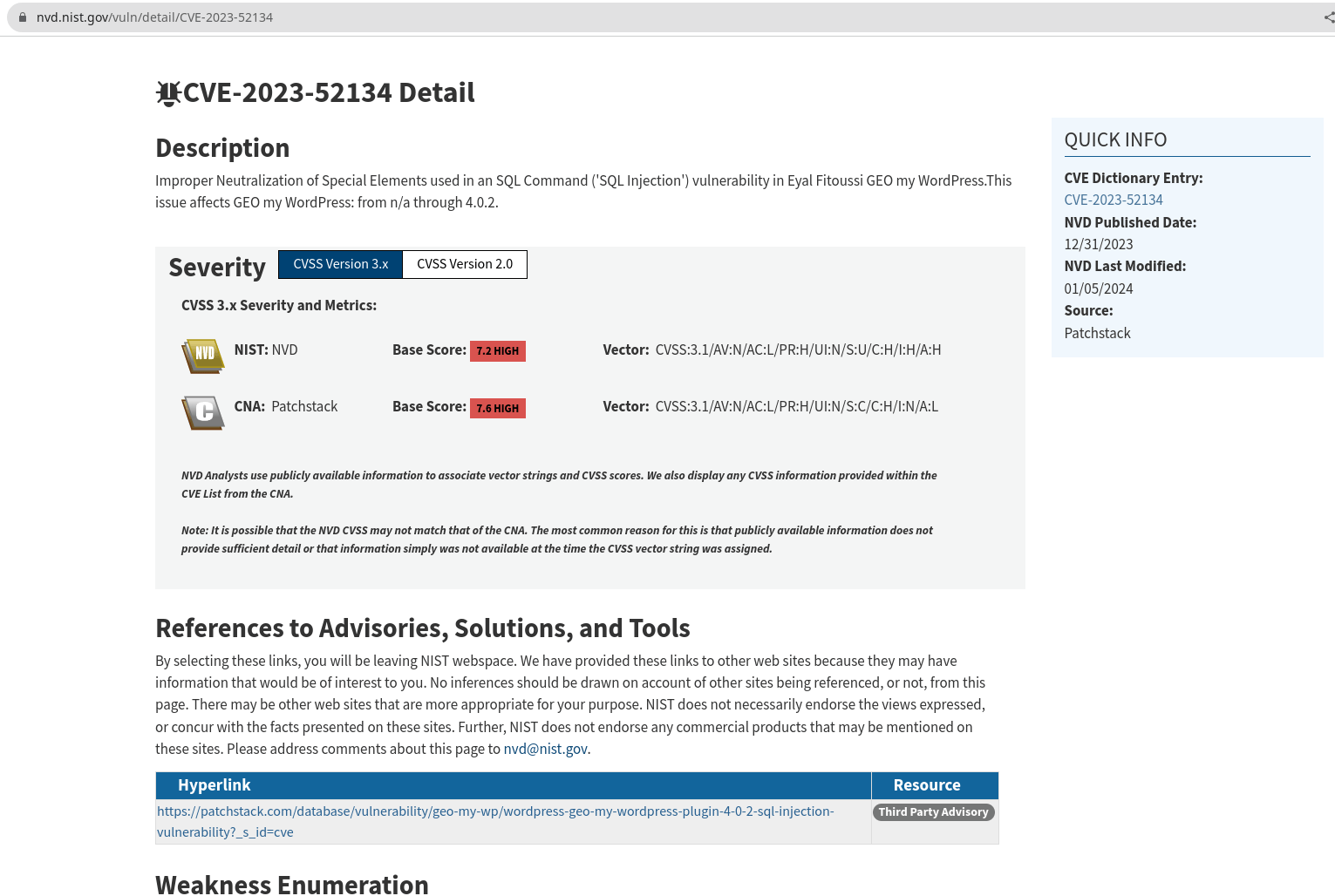
Going through the search results, I will select the first one from the National Vulnerability Database.
Other Reference: https://wpscan.com/vulnerability/eef61b02-2f18-4140-9778-46e52a1664c4/
From the above description, we can understand that the vulnerability is in the improper handling of the SQL queries in the "geo-my-wp" plugin, which leads to an SQL injection and is fixed in version 4.0.3.
As part of the security assessment, it can be taken further ahead for exploitation or can be reported directly based on the version information.
We have covered a huge base of different ways to scan WordPress vulnerability scanners to help you get started in identifying vulnerabilities.
Addressing Vulnerabilities and Implementing Security Measures
Knowing about the common vulnerabilities in WordPress sites is essential for effectively addressing and mitigating potential security risks.
Interpreting the scan results
Once the scan is complete, review all the results and identify potentially impactful security threats. Start addressing all the critical ones that require immediate attention, then move to high severity, followed by medium and low vulnerabilities to secure your site.
Implementing security measures to prevent future vulnerabilities
When addressing the vulnerabilities identified, follow best practices such as updating WordPress core, themes, and plugins.
Sometimes, we may not have the fix released by the vendor. This is where configuring a web application firewall is an additional line of defence to protect against common attack vectors.
In addition to addressing identified vulnerabilities, implementing security measures such as regular backups, SSL/TLS encryption, and security headers can help prevent future vulnerabilities and enhance the overall security posture of your WordPress site.
WordPress even offers to enable auto-updates of plugins, which can be updated regularly.
Enhancing the Securing of WordPress Sites
Check out the article below, which provides step-by-step instructions on how to secure your WordPress websites.

Automating Vulnerabilities Scans for Ongoing Protection
To maintain a secure and resilient WordPress site, it's essential to automate vulnerability scans for ongoing protection. The manual approach may not be feasible all the time.
The importance of regular and automated scans
Regular and automated vulnerability scans ensure your WordPress site is continuously monitored for potential security risks. By scheduling scans at regular intervals, you can stay ahead of emerging threats and proactively address vulnerabilities.
Utilizing alerts and notifications for immediate action
Configure alerts and notifications within your WordPress security scanner, if available. This helps you to receive immediate notifications of any identified vulnerabilities. It allows you to address security issues and prevent potential exploitation immediately.
Analyzing your WordPress security needs:
Using WordPress security plugin (DIY)
Website owners who would like to do it themselves can use any WordPress security scan plugins to get started.
As the requirements grow or you need to handle sensitive customer data or when managing multiple websites that require dedicated time to focus on business, seeking professional assistance might be beneficial to reduce the potential impact of data breaches on your business. Here, you could opt for an online subscription or hire a professional service.
Seeking professional vulnerability management services
Professional vulnerability management services offer a wide range of expertise, advanced tools, and proactive monitoring to identify and address potential security threats, providing peace of mind and enhanced protection for your website.

Conclusion
The above information can help you empower yourself with proactive WordPress security scanning measures to maintain a secure and resilient website. For website owners, I would recommend to get started with Jetpack Protect. Security Professionals or Ethical hackers who want to conduct vulnerability assessments, starting with the wpscan and Nuclie scans, would be a good start. By understanding the importance of regular vulnerability scans, choosing the right tools or plugins, and implementing best practices, you can take control of your website's security.
Additional References
Check out the bookmark below to learn more about the additional WordPress website security scanners online.

WordPress Security Scanners


