Lab Setup - Docker DVWA

If you're interested in learning and practicing web application security skills but not sure where to get started, this section will walk you through setting up the lab environment of the DVWA docker image, which is one of the practical vulnerable applications for learning web application security skills.
What is DVWA?
Damn Vulnerable web app or Damn Vulnerable Web Application (DVWA) is an intentionally designed vulnerable application for pen-testers and security experts in learning and testing web application security in a legal environment. It is developed using PHP/MySQL and can be deployed easily using an Apache server.
DVWA Git Repository
dvwa git
DVWA can be installed in multiple ways, such as using code from GitHub, Vagrant, or a Docker image, etc.
It is recommended to host the vulnerable applications in a host-only environment to prevent compromising other systems on your network by attackers.
You can even view the source code or contribute to the DVWA project. It's an open-source project.
For simplicity, we will be using our systems and pre-built docker DVWA image, which is publicly available, rather than setting up the whole stuff by ourselves. By running the DVWA docker container, we can save a lot of time and jump-start learning application security and penetration testing directly.
Requirements
- Docker installed & enabled on your Laptop/Desktop
- Any Operating System (OS) Linux/Windows/Mac
I am a GNU/Linux user, so most of the commands you will see from here on will be based on Linux (Debian), and similar commands do apply to other Linux flavors like Ubuntu and Mac with minor tweaks.
For Windows users, you can use either PowerShell or git Bash, where similar commands can be executed, or even the Windows Subsystem for Linux can also be used.
Verify Docker Setup
$ docker --versionOutput:
Docker version 20.10.17, build 100c701If the output is similar to the above, it means the docker is installed on your system and good to start.
For users whose docker is not installed, please visit the Get Docker page shown below.

Manage Docker as Non-Root Users (Linux-based OS Users)
For users who are using docker on Linux-based operating systems, we need to take one more additional step to ensure we can manage the docker image as non-root users.
After installation of docker, create a docker group and add the newly created user to the docker group.
$ sudo groupadd docker
$ sudo usermod -aG docker $USERNow log out of the user account and log back in again to verify you are now able to manage the docker instances from non-root users.
$ docker run hello-worldOutput:
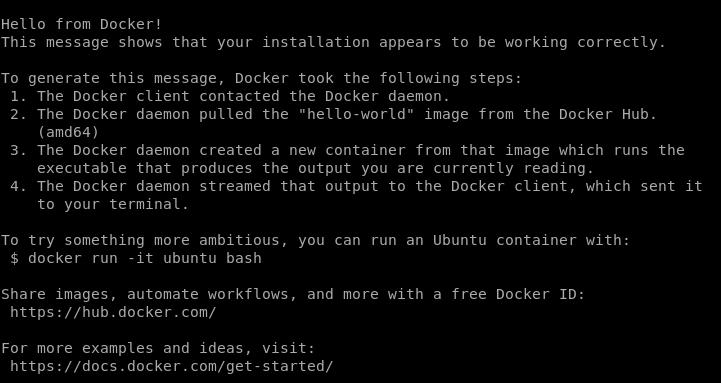
The above output confirms that we can manage Docker with non-root user privileges. More details can be found on the post-installation docker page below.


Benefits of Local DVWA Environment
- Practice any time.
- Ability to test any customized payloads or exploits.
- It can be used to test the effectiveness of Web Vulnerability Scanners or Automated Tools
- It can be used for Teaching.
- Ability to test custom security fixes.
Running DVWA docker
I hope your Docker environment is configured so we can start working. Here, we will use the Docker image, which has already been built and hosted in the Docker Hub.
Damn Vulnerable Web Application Docker Image:
https://hub.docker.com/r/vulnerables/web-dvwa/
Command:
docker run --rm -it -p 80:80 vulnerables/web-dvwaThe above command will download the docker image for the first time and will start immediately on port 80 after downloading it. Click here to verify.
If you are using port "80" for some other service in your operating system, you can change the docker container port to some random one (say 8443). Update the -p value with -p 80:8443. Ensure the updated port is used in the URL while accessing the DVWA web application.
To manually view, open a browser and visit "http://localhost/", you should be able to see the output as shown below:

The image will start displaying the console logs of the operations being performed on the DVWA website for reference.
Stop the running Docker image anytime by typing Ctrl - c in your console.
DVWA Admin Password
Now log into the application using Username admin, Password as password, Navigate to Setup DVWA ⇾ click on Create/Reset Database button.
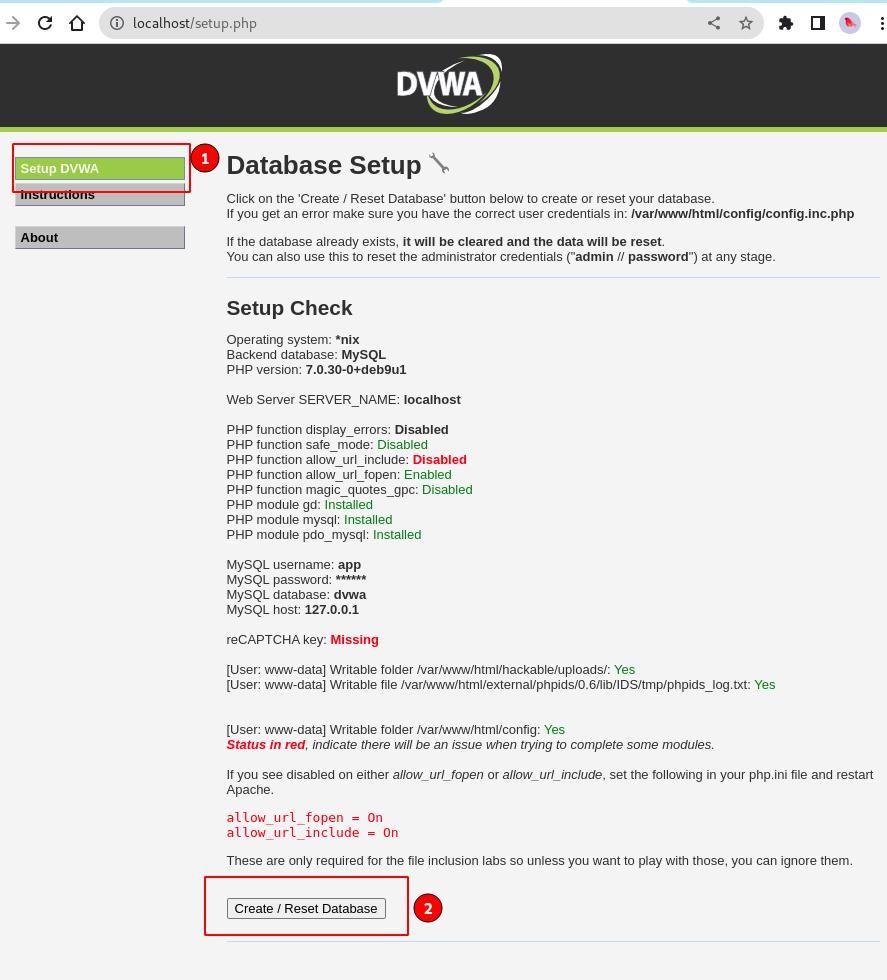
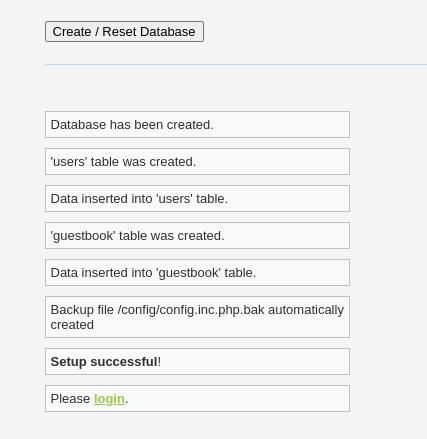
We can observe that the database has been created with a users' table. Some sample data is also inserted into the tables for our testing purposes.
Damn Vulnerable Web App Walkthrough:
Log into the DVWA application and observe most of OWASP's top-known vulnerabilities that have been created so you can get started. They are displayed as shown below.
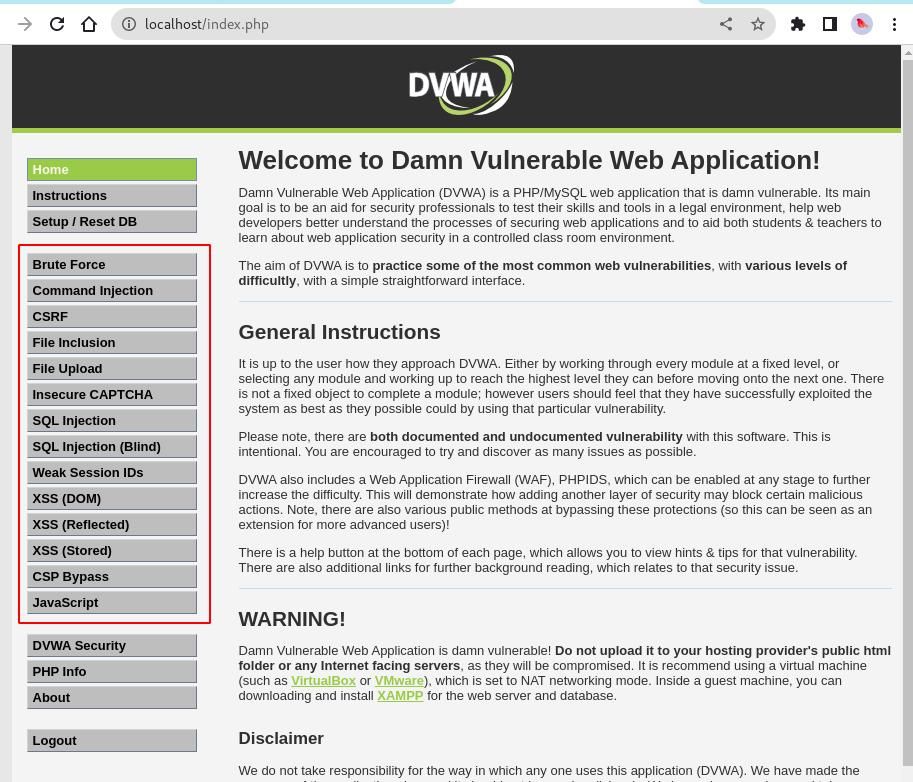
Our practice lab environment is up and is good to go.
From the above screenshot, you can use the DVWA to practice and get hands-on experience with known vulnerabilities, such as Brute Force, Command Injection, CSRF, XSS, etc.
Click on any vulnerability in the left-side menu, and the application will load the vulnerable page. All pages simulate close-to real-time application behaviors and provide hints to help you narrow down and use the correct type of vulnerable payloads for exploitation.
Remember that all our changes will be lost once you stop the DVWA docker image. You might need to repeat the above steps when you start. This is how the docker is designed, and it also allows us to begin with a fresh environment without worrying about previous changes.
The docker image needs some more tweaks, but we will do them when needed based on the type of attack we are discussing.
DVWA Security Levels
In the DVWA application, there are multiple levels to test any specific vulnerability, ranging from Low to Medium to High and Impossible.
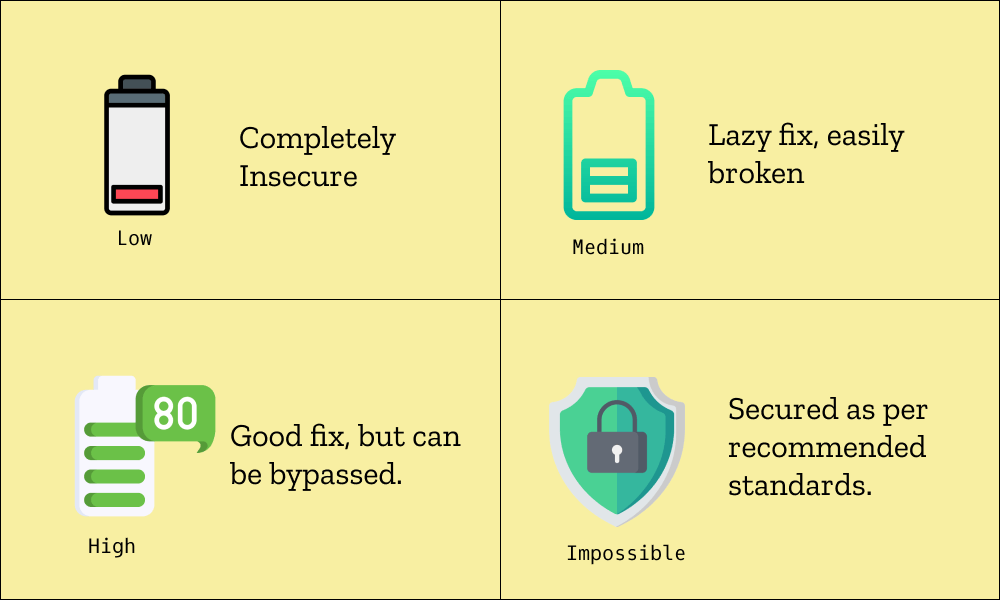
These levels help you build skills by understanding each scenario. First, you learn about the attack itself. Then, you will know how broken fixes are implemented and how they can be bypassed. Lastly, you will learn the best way to secure a particular functionality.
It is recommended that you go step by step. I still use it today to test specific payloads before they are applied to real-time applications as part of security testing.
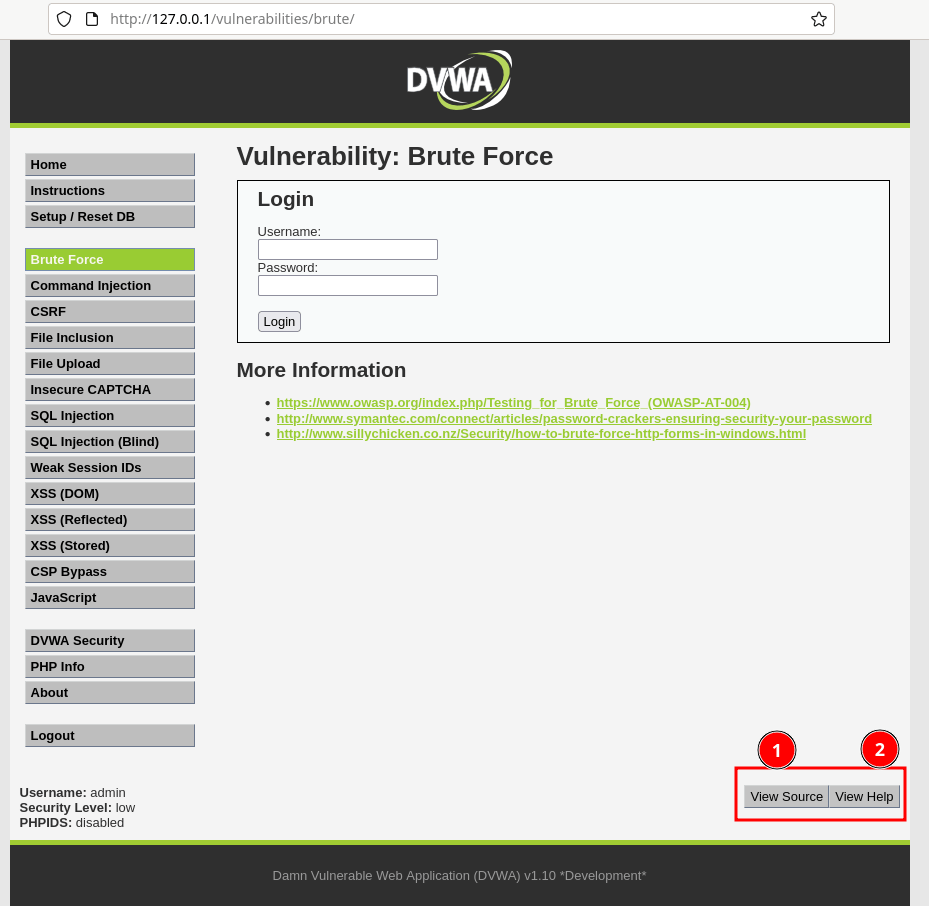
DVWA View Source and View Help
The DVWA application is mainly designed as a learning platform for application security. It also allows us to view the backend code for knowledge purposes.
Navigate to any vulnerability in the menu. Say the "Brute Force" menu item in the sidebar. On the same page, click on the "View Source" button at the bottom.
Similarly, the "View Help" button or "More Information" section can be used if you struck somewhere as initial help.
I hope the above information helps you to get started with a damn vulnerable web app docker.
If you want to learn about some basic web foundations before jumping into web security vulnerabilities, refer to the bookmarks below.

What is a Web application, and How does it work?

HTTP Basics
FAQ's
How to log into a damn vulnerable web app login?
You can use the credentials like username as admin and password as password.


