Challenge 3: XSS bypass Blacklist HTML tags
Using the XSS fundamentals learned will look at how poorly implemented input validations can be bypassed with a custom-crafted xss payload.

Welcome back to learning Cross-Site Scripting(XSS) with the Kurukshetra. An app built by d4rk36.
Before we start, ensure the Kurukshetra lab is up and running if you have not set up your lab yet. Feel free to refer back to the below link.

XSS Vulnerable App - By Design
We walked through stored and reflected XSS in a previous couple of articles. In today's article with those foundations, let's dive into the practical labs and start learning.
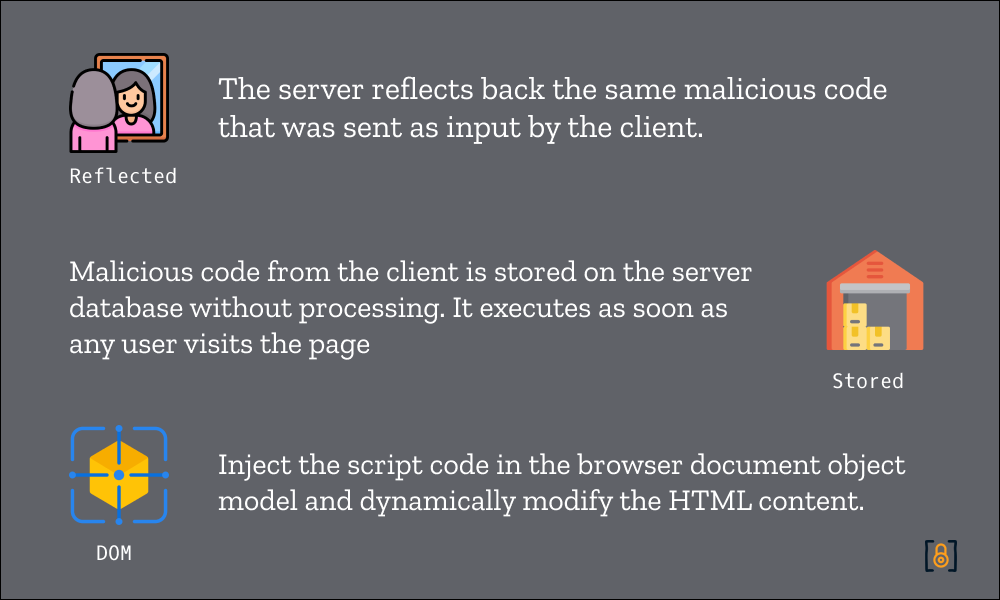

Practicals - Reflected XSS
Post setting up the lab, visit http://localhost:8066 and ensure it's accessible, then navigate to "XSS Challenge 3".
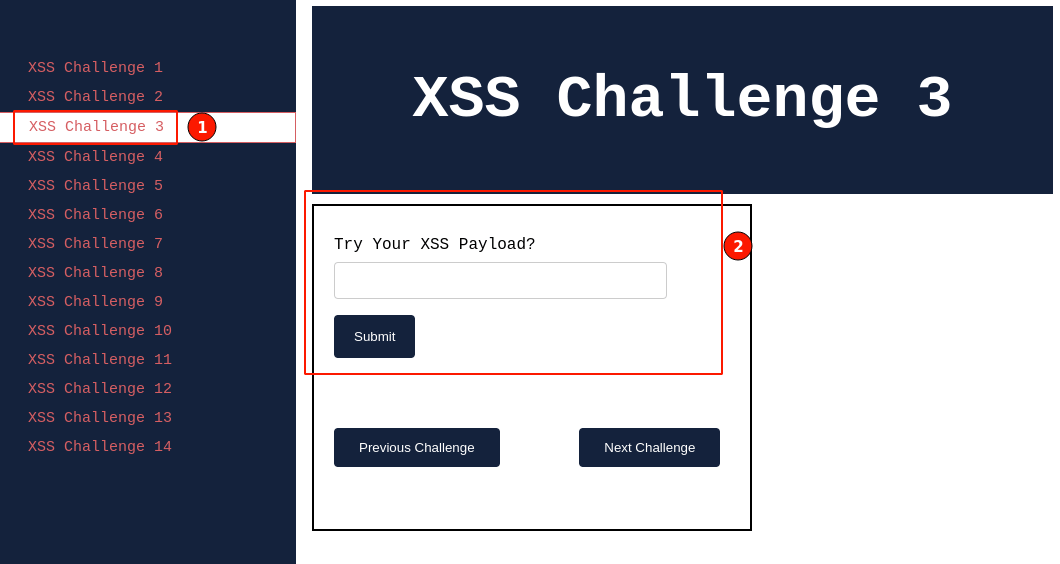
Let's try it with the XSS payload used in our previous articles and observe how the application behaves.
Payload Try 1: Classic
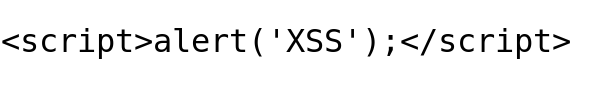
Output:
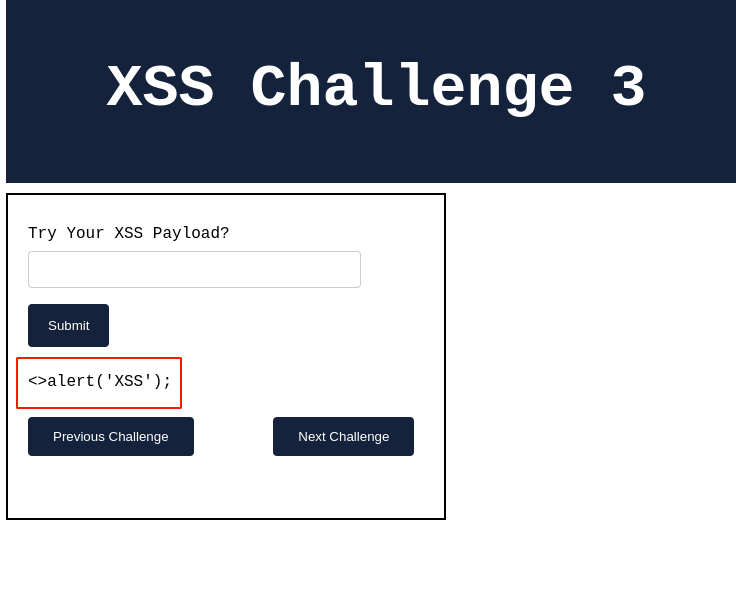
From the above observations, the application no longer gives pop-up messages but instead prints out the partial string from our given payload. Which indicates that our XSS payload is no longer working.
To evaluate further, click "View page source" to understand how our injected payload string is loaded in the HTML response body.
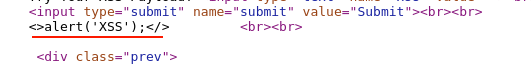
I can see that there is some kind of filter kept in place by the application that removes the word "script," which breaks the HTML syntax, and the browser treats the following data as just text and displays back the partial string.
Can we assume that the vulnerability is fixed? No
The developer leveraged a technique called "Blacklisting" to secure the application from exploiting the XSS vulnerability. However, this approach has limitations, and it can still be bypassed.

TIP - 1
HTML is case-insensitive, which means we can try it by changing it to upper case or small case letters or even combining small and upper case letters together, as given below.

Payload Try 2: Case-Insensitive
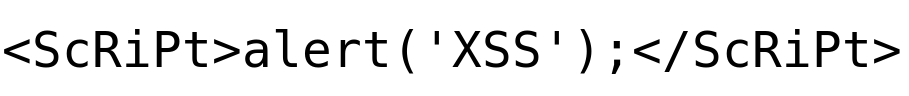
Output:
It looks like this technique also failed. The application seems to be filtering out the lowercase and uppercase script tags that were inserted.

TIP - 2
Javascript functions can be triggered for execution in multiple different ways, not necessarily that only the HTML script tag is needed all the time.
One of the ways to execute the javascript "alert()" function is using the HTML SVG tag, which is generally used for loading the vector graphics file on the HTML pages.
Example:
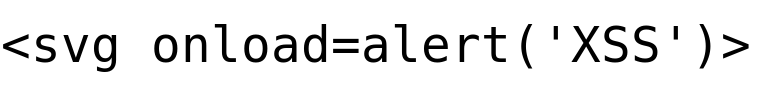
The HTML Attribute "onload" is one of the special words used to control the behavior.
In the above example, the HTML attribute "onload" is assigned to a javascript function "alert()" which runs immediately when the HTML SVG tag is loaded.
Let's go ahead and check out the things in action.
Payload Try 3: HTML5 Tags
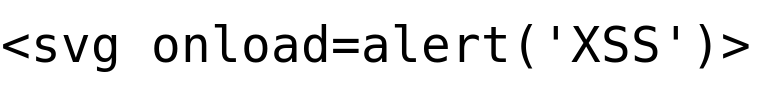
Output:
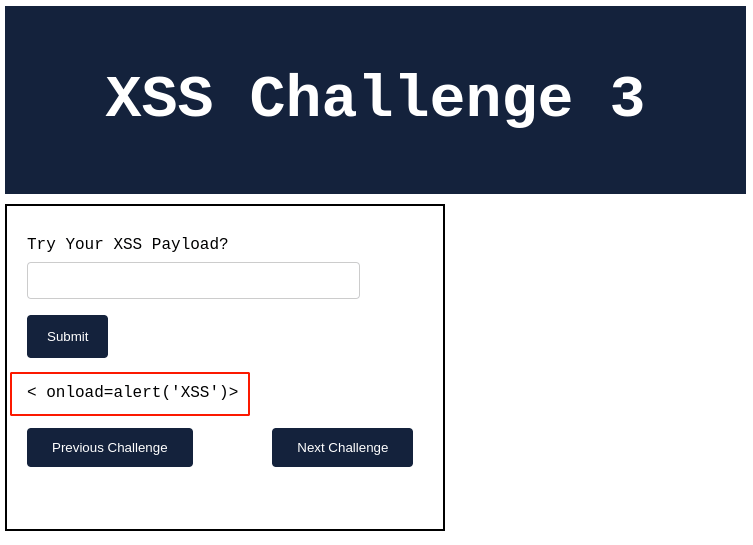
This attempt also failed, as the application filters out multiple HTML tag strings. i.e., svg, script, img, etc.
From the above example, we can see that the HTML attribute "onload" is being loaded without any filters and displayed back as keyed in.

TIP - 3
Not all HTML tag strings can be blacklisted. Some might break the entire HTML page itself and application functionality.
For example, the HTML Body tag is needed most to load the page's content. HTML Style tag, which is used to beautify the page, etc.
We shall improvise the previously used payload with the HTML Body tag.
Payload Try 4: HTML5 Tags
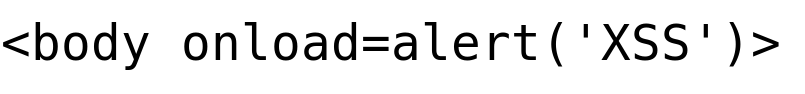
Output: pop-up message
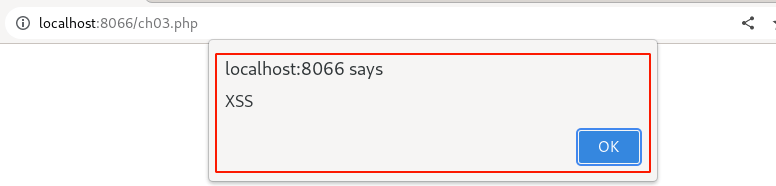
yay!!! 🎉 This time, our XSS payload worked, and the application displayed the pop-up message.
To further confirm, Click "OK," then right-click and select the "View page source" code to see how our payload was injected and aligned with the HTML response code.
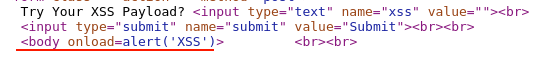
You should be able to find out that our injected payload is rightly aligned, HTML attribute onload event is triggered immediately. Therefore it indeed executed the javascript code.
Through this, we have successfully solved the XSS challenge 3.

Summary
In this article, we learned how poorly implemented validations can still be bypassed by improving the payload and trying different possible combinations. The blacklisting approach is helpful for a quick fix but is not foolproof, which must be updated whenever a new payload has been reported. Additionally, we covered many tips and techniques that can help you improvise your XSS identification skillset.
Keep learning!! :D

