DVWA - Brute Force Attack and Prevention Explained
This detailed guide explains Brute Force Attacks, how they work, and ways to prevent them. You can also explore a demo to understand the concept better and discover effective prevention mechanisms to safeguard your online security.

Brute Force is one of the security vulnerabilities which is commonly seen. This article will demonstrate the brute force attack on the Damn Vulnerable Web Application - an intentionally designed vulnerable application. In addition, it will cover how they work, the potential impact, and effective ways to prevent and safeguard your online security.
The following post is part of learning application security with the DVWA application.
Before jumpstart, ensure the docker DVWA application is enabled, configured, and accessible.
What is a Brute Force Attack?
A brute force attack is a trial-and-error method in which every possible combination of commonly used words, usernames, and passwords is tried out, hoping any of them will work.
Brute Force attacks are aimed at guessing commonly known files on the web server, breaking into email accounts, guessing remote services SQL or SSH server credentials (online), cracking password hashes (offline), etc., to gain unauthorized access to sensitive data or compromise security.
It would require a good amount of computing resources and time. #️⃣
The screenshot below from Cloudflare demonstrates how long it can take to crack a password based on the number of characters.
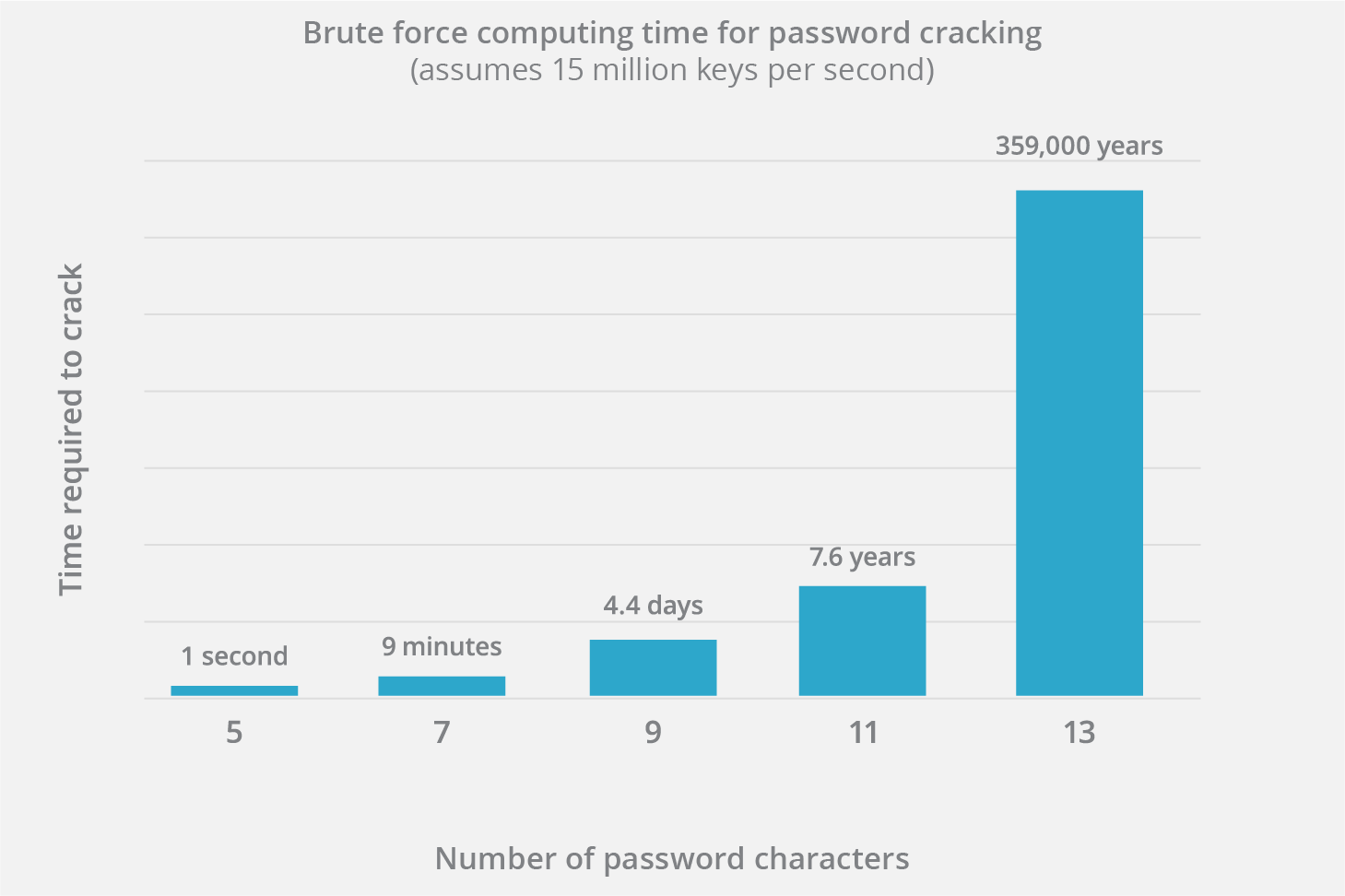
Today's hardware helps us crack a hashed password of 5 characters or fewer in seconds. The one with 12 characters or more, combining small letters, upper-case letters, special characters, and numerics, takes years to crack. The bigger the password, the more time it takes to crack using a Brute Force attack.
Think wisely, how much time you would like to spend for any brute force attack. A day or two may be good, but years and decades may not be worth enough.
Speaking on behalf of security assessments, we will be spending days or weeks. But attackers do have all the time they want.
How do Brute Force attacks work?
Brute Force attacks are performed using automated tools or software. A massive list of dictionaries containing common passwords, usernames, words, etc., is generated and given to the tool as input.
The tool keeps interacting with the service and tries out the dictionary entries one by one until a valid match is found, at which point it stops.
During this process, the attacker uses large dictionary data sets until the correct combination is discovered and successful access to confidential resources is obtained.
From now on, we will use the "Burp Suite" as an ideal tool for all our brute force attacks and to keep demos focused. If you would like to learn more about the basics and usage of the tool, Check out the following post on BurpSuite Overview.
Next, I will be using a small custom dictionary of usernames and passwords for fast brute-force results, which will be performed later.
admin
administrator
user
john
dvwa
bob
alice
root
superuser
superusernames.txt
admin
admin123
password
password123
user
user123
administrator
passw0rd
r3m3mb3rM3
admin123$passwords.txt
Brute Force Attack - Demo
The DVWA application has a Login page functionality that can be used to brute-force and find the right match of user credentials, simulating the attackers to compromise the application.
Let's go ahead and simulate the steps of an attacker and see if we can break in.
In information security, it's all about chaining up every piece of information you know, experimenting with it, and confirming if it works. In short, it lies in your creativity when using the information.
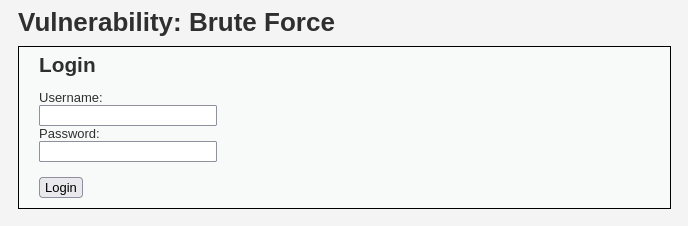
At the moment, we do not have any information about the username/password. All we see is a login page.
We will start with the Brute Force attack using the above dictionaries.
Let's start the BurpSuite tool and use the small custom dictionaries we created above. The tool tests for all possible combinations, and this method is scalable to thousands of combinations.
In the Burp Suite tool, navigate to the "Proxy" tab and click on the "Open Browser" button. A Chromium browser will be launched and will be displayed as shown below.

Log into the DVWA application using “admin/password” and navigate to the "Brute Force" item in the menu.
Let's try some known username and password combinations.
Say "administrator/admin123", "admin/admin123", "user/user123" etc. For all incorrect attempts, we keep getting the "Username and/or password incorrect." message.
Manually trying out is also known as a simple brute force attack, which is painful and limits the knowledge to oneself. This approach is time-consuming and isn't scalable.
If you found a valid login match this approach? Excellent. You perfectly guessed it. 👍
In Burp Suite, we need to capture the Login request. I will enable the Intercept option to capture a specific login request so we can perform automated operations using it.
To enable it, navigate to Burp Suite "Proxy" tab ⇾ "Intercept" ⇾ toggle on the "intercept off" button. It immediately turns to "intercept on" as displayed below.
Key in some random data in the username and password file, then click on the "Login" button as shown below.
Once the Burp Suite receives an intercept request, you should be able to see the highlights immediately. Navigate to the "Proxy" tab. ⇾ "Intercept". You should be able to see a request similar to the one below.
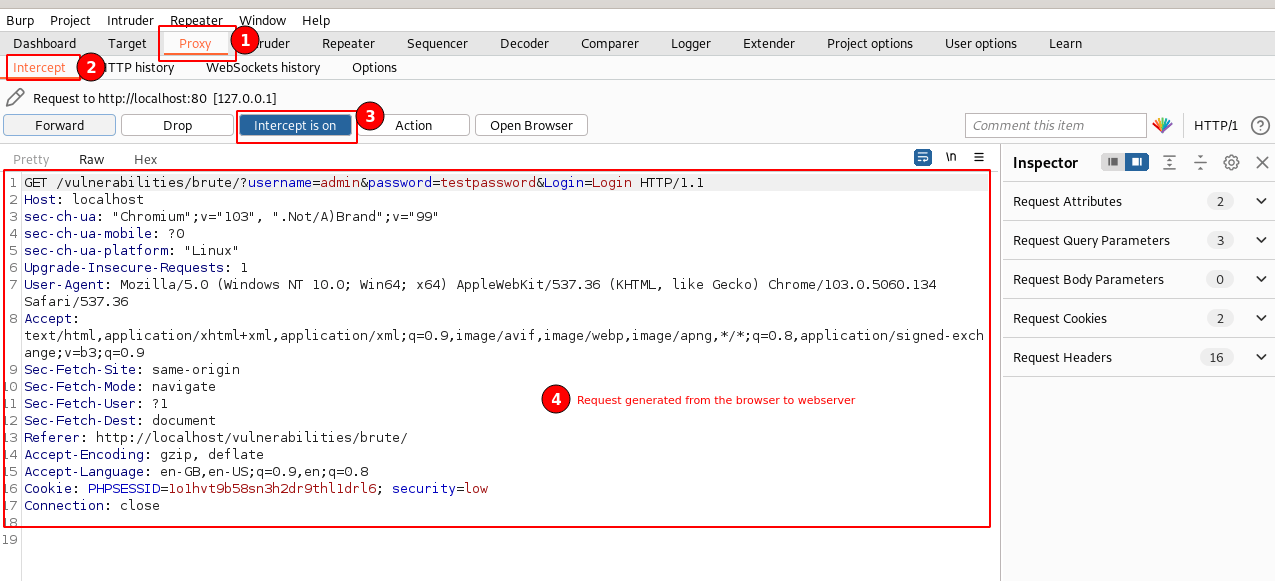
An HTTP GET method is used, remember the GET method doesn't have a message body. Therefore, all the parameters and values will be sent as a URL.
GET /vulnerabilities/brute/?username=admin&password=testpassword&Login=Login HTTP/1.1Here, we are trying to access a page called "/vulnerabilities/brute" and passing parameter values "username=admin&password=testpassword&Login=Login" to perform the login action required by the application.
If your credentials are valid, you will be able to log in successfully. Otherwise, you will receive an invalid login error message.
Now, click on the "Action" button and select "Send to Intruder".
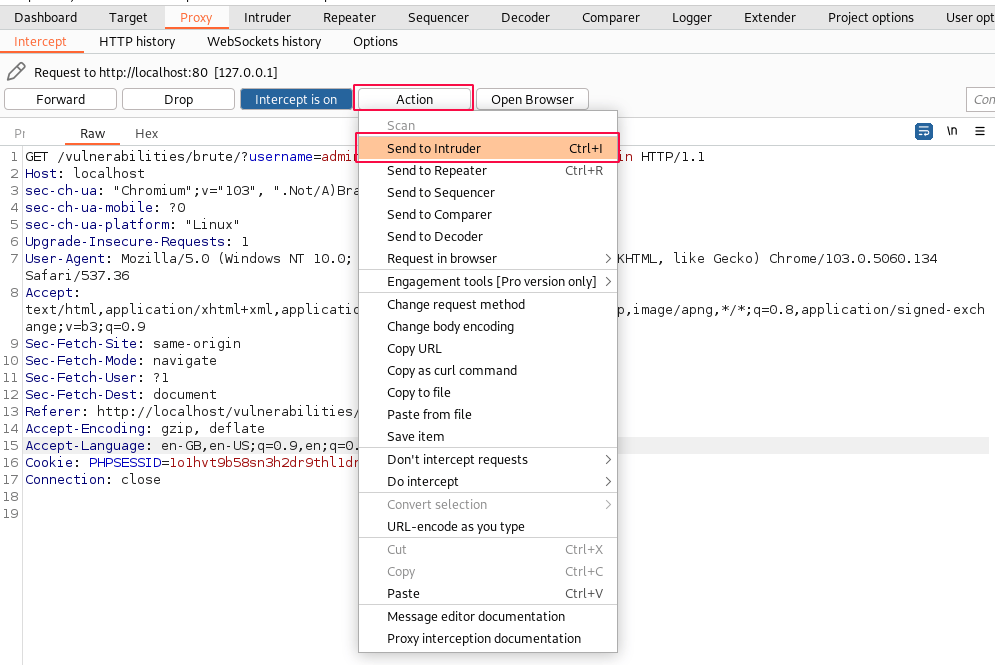
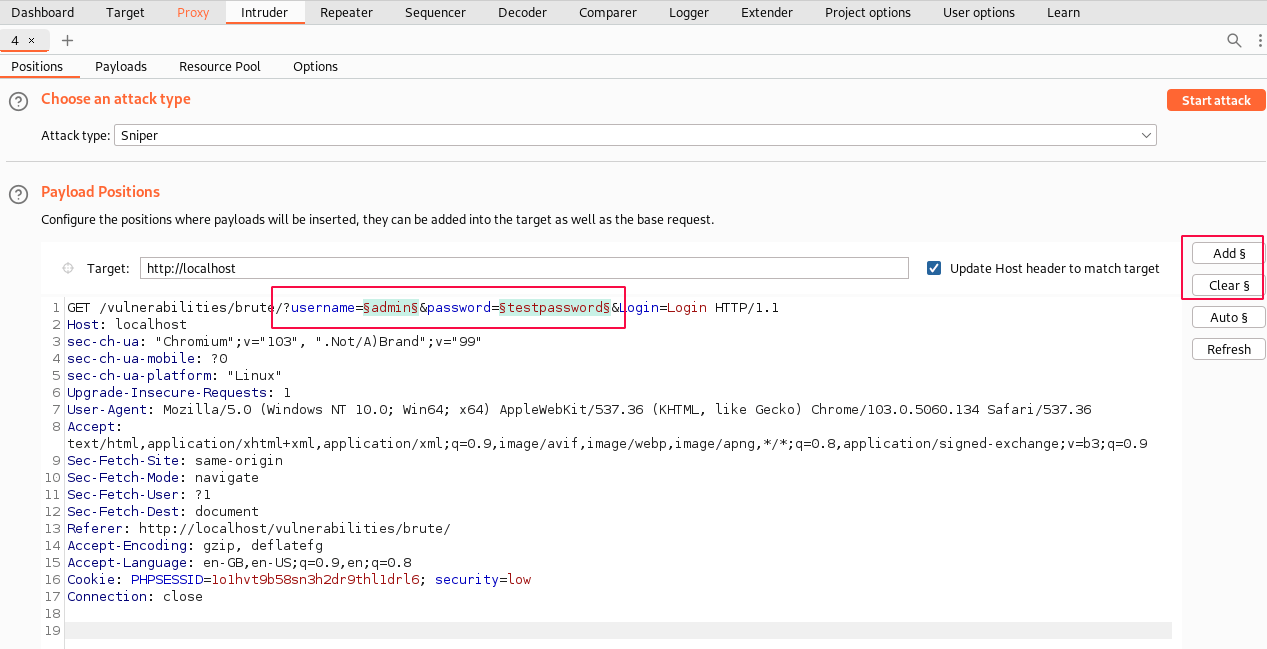
Switch to the "Intruder" tab, and you should be able to see the same request there. Under the "Positions" sub-tab, The tool automatically detects where all the changeable values need to be placed and highlights the five parameter values section for us.
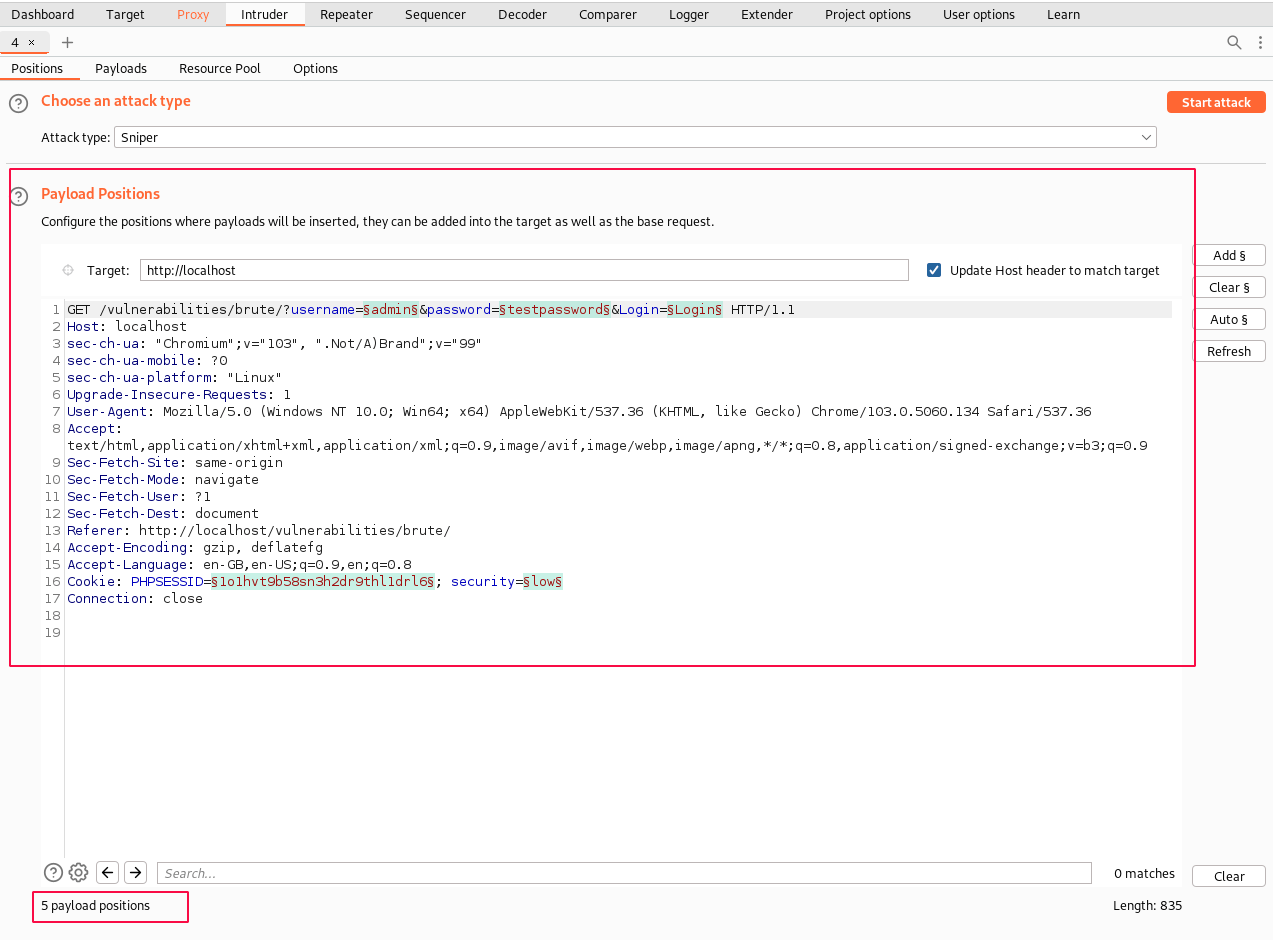
I will clear all the payload locations and select only username and password using the "Clear" and "Add" buttons beside.
Types of Brute Force Attacks
There are four brute-force attack types that are supported by the "Burp Suite" tool.
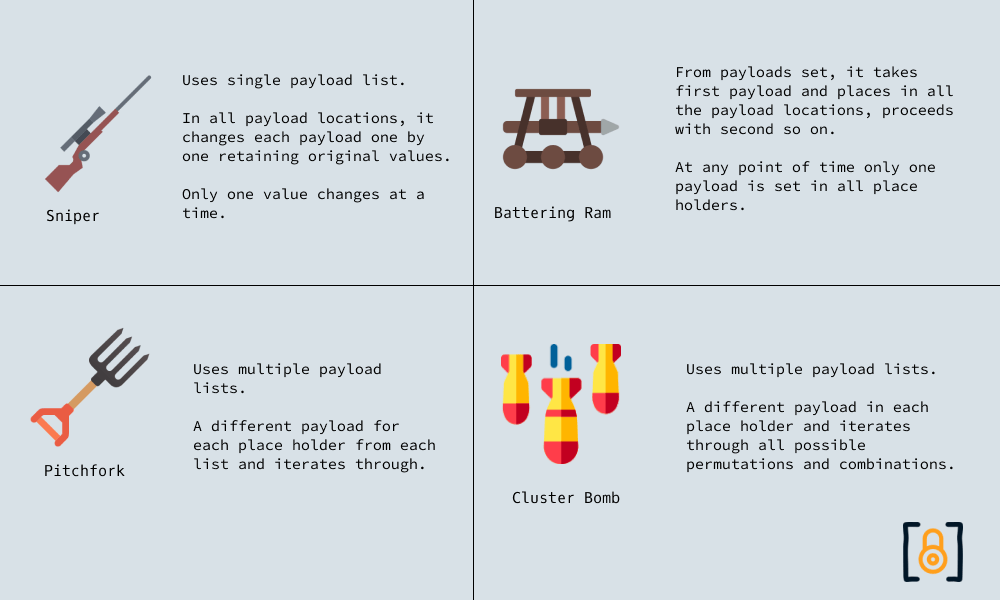
Cluster Bomb best suits our requirements. Set the attack type to "Cluster Bomb" and switch to the "Payload" sub-tab.
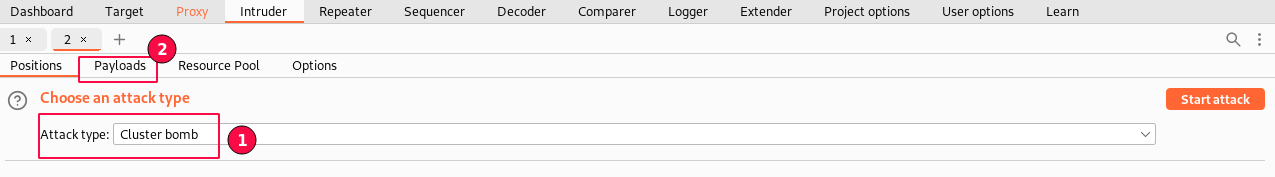
In the "Payloads" sub-tab, select "Payload Set 1", payload type as "simple list" and paste all the contents in payload options copied from the usernames.txt list.
This is for the "Username" values.
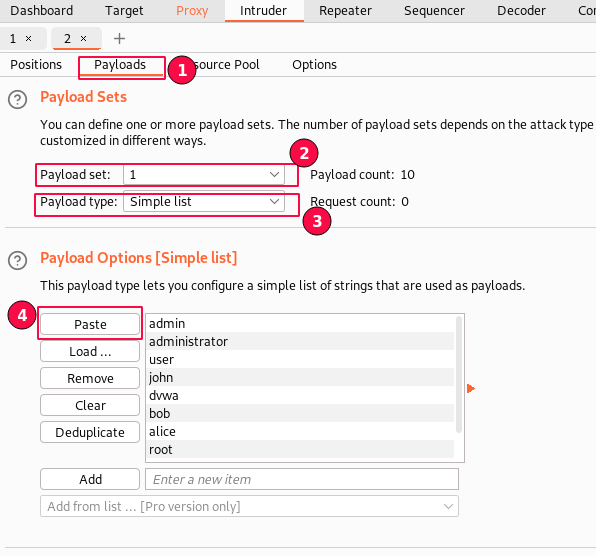
Second, select the "Payloads" sub-tab, set "Payload Set 2", set the payload type as "simple list" and paste all the contents in payload options copied from the passwords.txt list.
This is for the "Password" values.
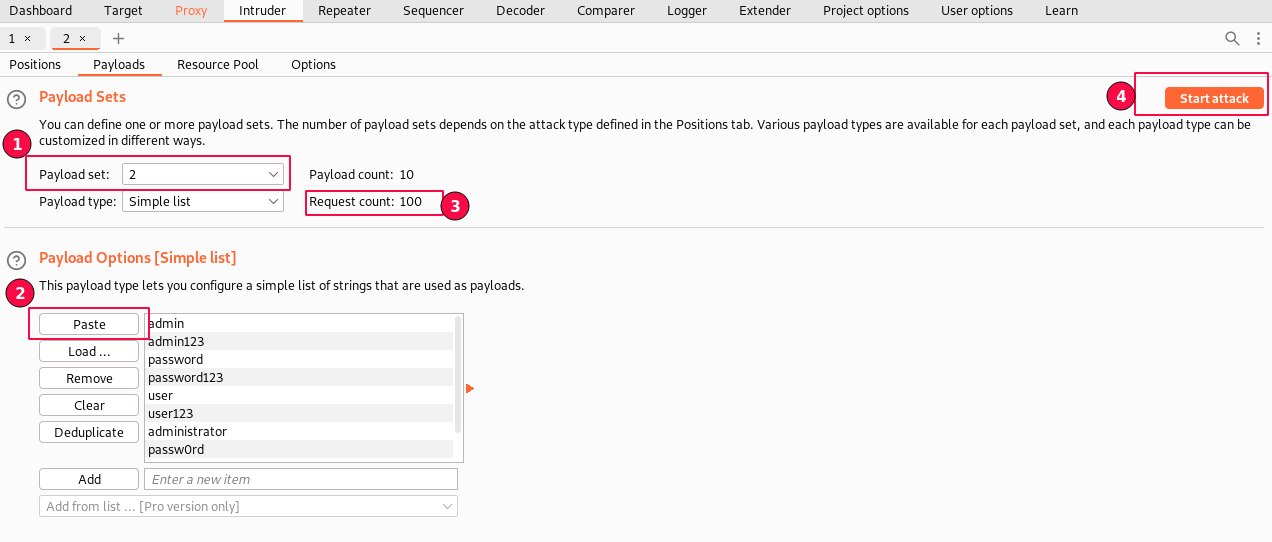
Observe that the request count is now set to 100. Using the two lists now, we will be trying out 100 possible combinations.
Lastly, click the "brute-force" button at the top right to initiate our brute-force attack.
In the BurpSuite Community edition it prompts with a warning box as some features are limited. Click "Ok" to continue.
An intruder window pops up, and the payload information and request status will be displayed below.
If you take a look, we can see we are getting a 200 status for each request, which means "200 Ok".
How do we know which payload combination worked and which hasn't?
One way is to click on each request with a 200 Ok status, select the "Response" sub-tab, and search for the string named "Username and/or password incorrect". We know this belongs to a failed login attempt.
If the string isn't present, it means the credentials combination worked, and that would be our match.
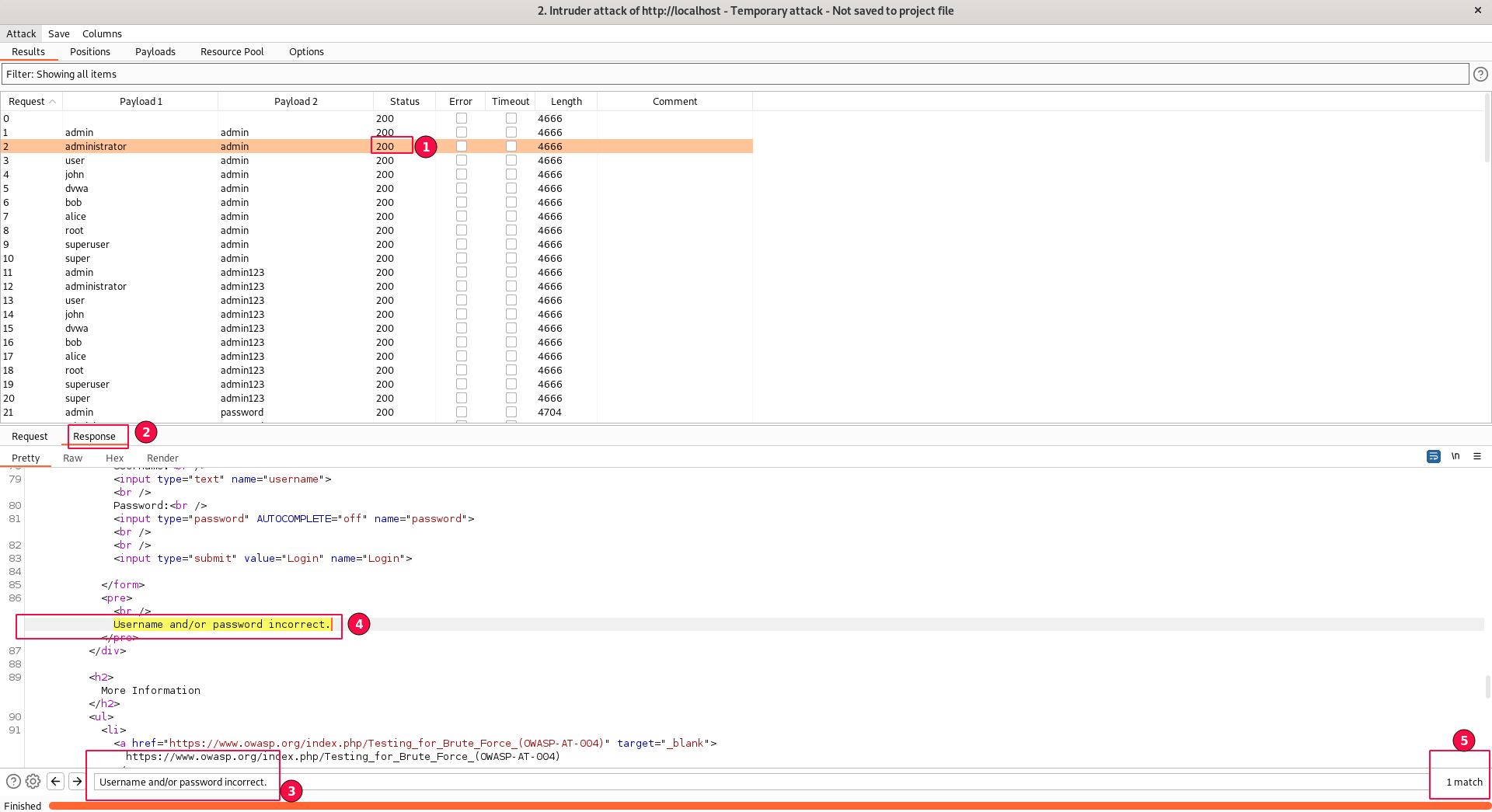
BurpSuite Intruder figured out there is one positive match on the bottom right side of the screenshot. This is a time-consuming approach.
Focus on the size of the length as shown below. For all incorrect attempts, the response message length is the same "4666". Check one of a different length, i.e., 4704.
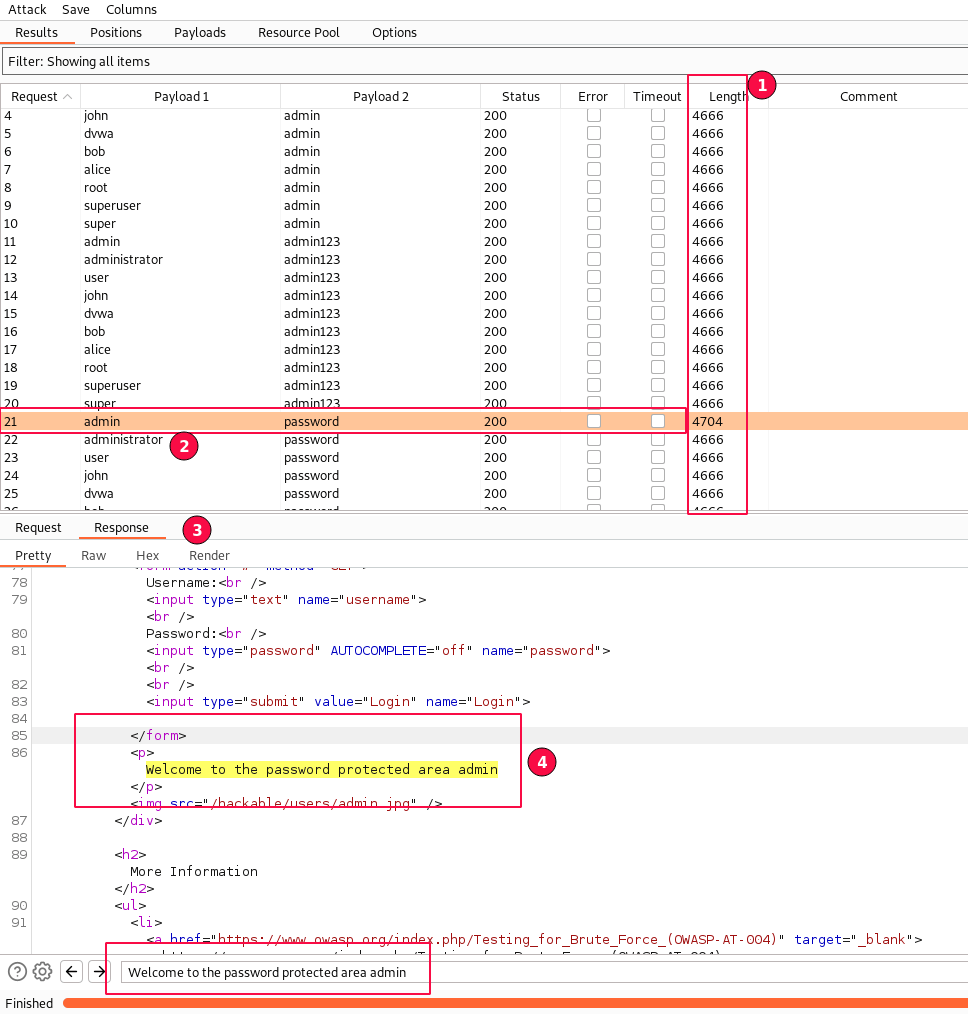
Observe whether the username/password combination "admin/password" worked. Navigate to the response sub-tab, We can see the "welcome to the password protected area of admin" message.
Hurray!! we found the right password match! 👏
Password Match Verification
It is always good practice to re-verify the security bug before we report it.
Make sure all the Intercepts in the proxy tab are toggled to off. Then, let's return to the brute force page and verify our match to confirm our results.
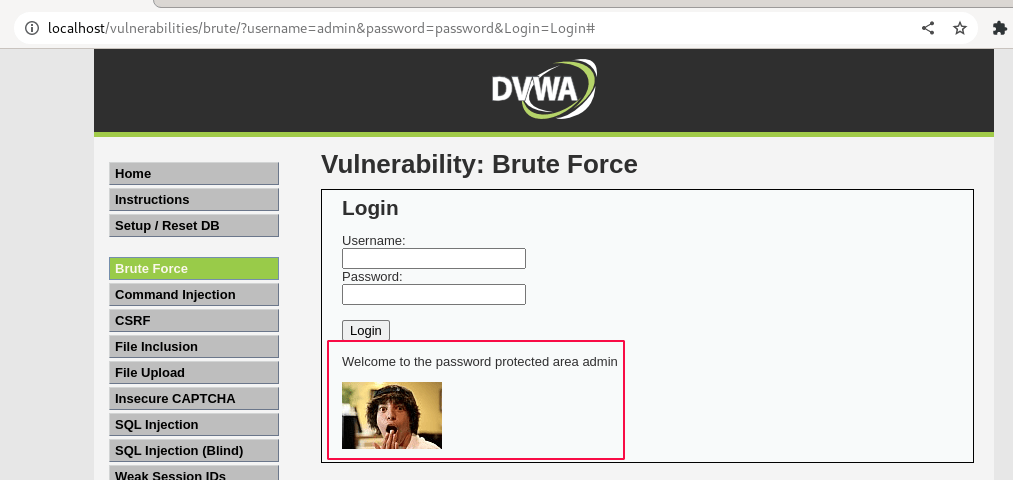
Yep, our newly found password combination worked.
Excellent! We found a security bug using a Brute-Force attack, i.e., a guessable username and password.
You were able to learn a quick way to Perform a Brute-Force attack using DVWA. If you would like to learn more ways to perform brute-force attacks and how partial security fixes can be bypassed, check out the articles below.

Exploiting DVWA Brute Force Attack - Medium Severity

Exploiting DVWA Brute Force Attack - High Severity
I have used a short custom-built word list for demo purposes, Give a try with other lists. Search for "Brute-Force attack" or "Brute force wordlist", and you will find many resources.
Below are some lists from Github.

Github Brute Force wordlist
Impact of Brute Force Attacks
The impact of a successful brute force attack can be severe.
- Unauthorized access to sensitive information.
- Financial loss
- Loss of organization's reputation
- Leading to potential legal and financial repercussions for the affected individuals or organizations.
- Loss of customer trust, etc.

Preventing Brute Force Attacks
Security Researchers and web application developers need to be familiar with mitigation techniques. These skills can help them defend web applications from malicious actors.
So, let's talk about some ways to detect it and then mitigate it.
Patterns of Brute Force Attack
Some of the common patterns can help to detect brute-force attacks on our webserver.
- Too many requests originate from a single IP address within a minute or hour.
- Multiple logins of a single user account from a different IP address and province.
- Excessive usage of the server resources and bandwidth.
- Increased number of failed login attempts of various usernames and passwords.
- Logged into multiple user accounts from a single IP address. (i.e., guessable default password) etc.
The above is a small list targeting user credentials, but the patterns vary for other resources.
Defending Brute Force Attacks
Brute force attacks are difficult to stop, but with good measures, we can limit the attack surface.

Avoid Using Default/Guessable Passwords
One of the most commonly exploited techniques says some application servers come with pre-defined default passwords for the initially created accounts. (Say "admin/password")

Some companies follow an initial password with the company name followed by a number sequence. Say "ABCCompany123" or the special character "ABCCompany123$", some with established year appending at the end with a prefix of the usernames "Username2022" etc.
These are all unknown until someone figures them out. Once figured out, they are easy to try out with all the user accounts to which the user account has access.
Additionally, prevent users from using passwords such as "password", "admin123", "12345" etc.

Limit Login Attempts
One good practice is to limit the number of failed login attempts the user is allowed to make. Beyond 7 failed login attempts, the account is locked for a temporary time period. Like banks, beyond three failed attempts, the user account will be locked out for 24 hours. Or

Enforce a Strong Password Policy
A best-designed password policy like the use of a combination of small case letters, upper case letter, numerics, special characters will make it hard to crack for attackers.
Use of password managers wherever applicable.
Avoid re-using the same password.
The length of passwords is to be 8 or above.
Prevent the use of common dictionary words or guessable sequences.
Use of certificates for authentication rather than passwords.
Educate users about using a different password for all accounts.

Progressive Delay
This is also the best technique where the wait time keeps on multiplying with each failed login attempt.
Say, initially start with "60 Seconds" wait time at the first attempt, then 15 minutes of wait time for the second attempt, 60 minutes for the third attempt, and so on it goes.
Generally, some applications multiply wait seconds by 60 for each failed attempt.

Using Captcha
Captchas are used to filter automated bots or programs and prevent them from abusing the services.
Multi-Factor Authentication
Adding additional layers of verification makes brute force attack very tough. Using the OTP - One-time passcode, verification of token through email, or Security Questions before logging in makes it more difficult for attackers.
The attacker needs to compromise multiple sources to gain access to your user accounts which is very very tough but not impenetrable.

Storing Salted Password Hashes
Even though our application is secured in all possible ways, some third-party plugins or disgruntled employees may lead to compromise of the application and say the attacker was able to gain access to all the passwords in the database.
When a user enters the password say "admin123" it is not a good practice to store it as plain text. It must be hashed and stored.
hash(admin123) = GX8N365FMeK9hsRkW9Dl2S/ikcQNow add salt to the above hash. Where salt does not need to be a secret text but a random text. ( say "5MU63YzoOm7ig")
The Hash + Salt will be displayed as shown below
hash(admin123 + 5MU63YzoOm7ig ) = LL/0NIJmT2JcfCXkfOln62pj8HwThe salted hashes make it much more difficult for attackers to crack the passwords offline.
Even though the attackers have salted hashes, it would be tough for them to crack and re-use them. Meanwhile, requesting the user to reset the passwords in case of compromise makes it more secure.

Whitelisting
Whitelisting or Allowing a list is an approach of letting only what you trust and blocking all the rest from accessing.
Let's say for high privileged admin user accounts, employ a way to whitelist the login's from known IP addresses or authorized VPNs and restrict all others from accessing admin features.
This reduces a huge attack surface.

Using Web application firewalls
Configuring and using Web Application Firewalls (WAFs) protects web applications from a wide range of attacks, such as brute force attacks, denial of service attacks, and malicious input filtering, etc. Examples: AWS WAF, Cloudflare WAF, etc.
More information on blocking brute force attacks can be found on the OWASP site.
Conclusion
Understanding the basics of brute-force attacks and their potential impacts is crucial for safeguarding against cyber threats. By implementing robust security measures, such as strong password policies, multifactor authentication, and network monitoring, individuals and organizations can mitigate the risk of falling victim to a brute-force attack.
Using of captcha's can be inconvinient feature, but use it cautiously to prevent automated bots or from automated attacks. Hope by this you are familiar with what a brute force attack is and how it can be exploited. Keep Learning!! 😄


